What is PPTP VPN? How does it work, and what is it used for?

Because we know it’s a rather common question when it comes to VPNs, we will try to provide a complete answer for those of you wondering “what is PPTP VPN?” and how this protocol works. As we know, a VPN protocol dictates exactly how a VPN handles data and is a blueprint for everything a VPN does, so it’s important to know all their characteristics in order to make the best choice for our particular needs.
Table of contents
- 1 What is the PPTP VPN protocol?
- 2 PPTP technical details
- 3 How PPTP works
- 4 PPTP security, speed, compatibility and setup process
- 4.1 Is PPTP secure?
- 4.2 How fast is PPTP?
- 4.3 PPTP compatibility
- 4.4 PPTP VPN setup
- 5 PPTP versus other VPN protocols
- 5.1 PPTP vs OpenVPN
- 5.2 PPTP vs IKEv2/IPSec
- 5.3 PPTP vs L2TP/IPSec
- 5.4 PPTP vs SoftEther
- 5.5 PPTP vs SSTP
- 6 Bottom line
What is the PPTP VPN protocol?
PPTP stands for point-to-point tunneling protocol. It is a method of connecting to a virtual private network. It enables users to access certain networks from a remote location.
To better this, you should imagine your PPTP client establishing a connection to the PPTP server through which all your data travels to and from your device. This connection can be visualized as an encrypted tunnel through which your network data is encapsulated and placed into an IP envelope. The data will be treated by any devices on the network the same way as an IP packet would.
The point-to-point part refers exactly to this: it allows a user to connect through the internet from a certain point (his home computer, for example), to another point (his company office network), without having to be there physically.
Tunneling has to do with the manner in which the PPP (point-to-point protocol) is combined with the internet technology to form the PPTP protocol. Through encapsulation of the data packets transmitted over the network, PPTP establishes the tunnel connecting the client device to the VPN server.
PPTP was designed in the 1990s when high-speed internet usage was on the rise. Windows, along with some other companies, worked on a viable solution for their customers which would assure good internet and intranet access, all the while offering basic data encryption.
In 1999 the RFC 2637 was published for PPTP. Having been designed to function well across all Windows devices, the PPTP protocol was easily accessible to the average customer. Combined with the high internet speeds it offered and its easy-to-use features, this protocol became widely used among small businesses at the turn of the 21st century.
Currently, the PPTP VPN protocol is still used by many. A major factor behind this is the fact that Windows, Mac, and Linux devices all have this protocol integrated into them and can thus operate it without additional files needing to be installed.
Although the protocol is no longer deemed safe, many choose to use it for unessential purposes, or simply because it’s the most accessible to them. However, for the modern user who is the least bit preoccupied with his information’s security over the internet, this protocol should most definitely be avoided.
PPTP technical details
Now that we’ve answered the question “what is PPTP VPN”, you’re probably wondering exactly how PPTP works. Well, for those of you interested, I will explain.
The PPTP protocol appeared as an extension of the PPP protocol and works in a similar way. For this reason, I will begin by presenting some details of the PPP.
The point-to-point protocol (PPP)
PPP is a fairly old protocol for communications which was described in RFC 1661. It is a data link layer 2 protocol, and it is used for making connections between two points (computers). For those of you who don’t know what “data link layer 2” means, it is referring to the second layer of the OSI (open systems interconnection) model.
This protocol offers data encryption, authentication of connections, as well as data compression. PPP has 4 main components:
Encapsulation (also called framing): PPP is capable of transmitting multiple layer 3 packets on even a single link. Thus, the protocol encapsulates in frames the network layer packets.
The link control protocol (LCP): The role of this protocol is to establish, preserve and configure data-link connections, as well as to terminate the links when the time comes. It also takes care of negotiating the link conditions and parameters. In order to do all this, LCP has several steps to go through. These are:
- Authentication: Authentication protocols are used by LCP. The password authentication protocol (PAP) and the challenge handshake authentication protocol (CHAP) are used, usually the latter. A third option is the extensible authentication protocol (EAP), whose details are presented in RFC 2284, and more recently in RFC 3748. These protocols ensure that the server device is convinced that it is communicating with the correct computer.
- Compression: In order to send data faster, LCP makes use of the compression feature, thus also sparing bandwidth. The data is compressed on the sender’s side and after being received is decompressed.
- Multilink: This option allows the merging of two links into a single link. While this option can perhaps quicken the data transfers, it does increase the possibility of receiving information packets in the wrong order.
- Error detection: LQM (link quality monitoring) is a tool used by LCP. This tool supervises interfaces and detects whether any of them exceed the admitted error percentage. If the threshold is exceeded, LQM will deactivate the problematic interface.
- Loop connection detection: another neat feature of the PPP is that it can find loop connections and terminate them. This is done using a “magic number”, which is sent through the connection. If it is looped, this magic number will return from where it left and will be detected.
Network control protocol (NCP): PPP offers the possibility for more than one network layer protocol to function using a single communication link. However, for each network layer protocol that is used, there must exist an associated NCP which configures and sets up their network-layer protocols. Examples of NCPs used by PPP are OSI network layer control protocol (OSINLCP), internet protocol control protocol (IPCP), internet packet exchange control protocol (IPXCP), and so on.
How PPTP works
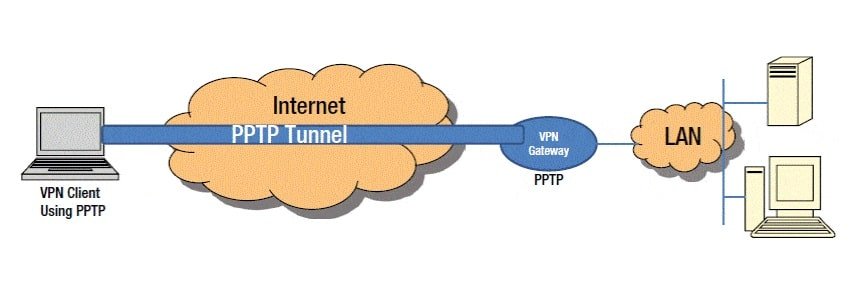
Now that we’ve amply explained what PPP is, let’s get back to PPTP, and find out just what makes it tick.
In general, this protocol was widely used by businesses in order to enable clients or employees to access their firm’s servers from their homes through the internet. Nowadays it is still often used by firms, but also by individuals looking for a quick VPN solution.
PPTP functions on the second (data) layer of the OSI model. The connection between the two devices goes through TCP port 1723, which uses the transmission control protocol (TCP). This protocol was built together with and for the Internet Protocol (IP). TCP offers information packet delivery in an ordered manner so that the information is accounted for.
Afterward, the data packets are made using the GRE (General Routing Encapsulation) process. GRE, a tunneling protocol produced by Cisco, allows for a large assortment of network-layer protocols to be encapsulated inside port-to-port virtual links. This is done using an IP (internet protocol) network. The tunnel is basically made by the data packets traveling to and from the client device and the VPN server.
PPTP security, speed, compatibility and setup process
Ok, so we now have an idea of how the PPTP protocol works, and understand the technicalities behind it. But is it still useful today, and if it is, is it safe? I will be replying to these and other questions in the next section.
Is PPTP secure?
Simply stated, the answer is no. This protocol is no longer considered safe as the encryption key it uses has been cracked by governments and criminals. It seems that this protocol was deemed unsafe almost from the time it was launched.
There are methods through which a PPTP server can obtain better security. One of these ways would be to switch from the standard (and otherwise compromised) CHAP (Challenge-Handshake Authentication Protocol), which has been shown to have fatal security liabilities, to the EAP (extensible authentication protocol).
EAP is a possible substitute, however, it uses public key infrastructure (PKI) which noticeably reduces speed, and can also be tricky to use.
While Windows did provide an update to the PPTP protocol (PPTP version 2), it still had its flaws. Since then, Windows has not invested in any further updates to the protocol and consequently, there’s been quite a number of security issues with the point-to-point tunneling protocol.
In conclusion, I would not recommend using this protocol if you care even just a little about the security of your data. It is widely accepted as a fact that this protocol has serious flaws, and provides little to no actual security for your information.
How fast is PPTP?
Interestingly enough, although it uses TCP and not UDP, which seems to offer faster internet speeds than the former, the PPTP protocol does offer one of the top speeds you’ll find among VPN protocols.
I’m not saying it’s the fastest, seeing as protocols such as SoftEther and IKEv2 also offer comparable speeds, but it is one of the fastest ones. That being said, this is one of the big reasons why this protocol is still actually used by some people.
PPTP compatibility
We come to the second biggest reason why the point-to-point protocol has been and is being used so frequently. It began to be widely used due to the fact that Microsoft implemented it into its devices. The protocol is often pre-installed not only on Windows devices but also on Mac, Android, Linux, as well as iOS devices.
People who were looking for a quick and simple VPN solution obviously turned to their most accessible option, PPTP. Unfortunately, although it does have some positive aspects, it is definitely not the best option any longer.
PPTP VPN setup
Many VPN providers still use the PPTP protocol to offer their services mostly because of the great speeds it offers. Oftentimes though, especially with the paid subscriptions, you should be able to opt for a different protocol, such as OpenVPN. If you are using a free VPN, you shouldn’t be too surprised if the protocol it uses is actually PPTP. Despite the fact that it is quite fast, the protection it offers is close to non-existent.
PPTP versus other VPN protocols

While I’ve already clearly stated that the PPTP protocol is not the best for online security, it may be helpful to see how it compares to some of the other main VPN protocols out there.
PPTP vs OpenVPN
OpenVPN is pretty much accepted as the best protocol out there. With decent speeds and good security features, there aren’t too many things it’s missing.
When comparing PPTP with OpenVPN, the main difference that stands out is the fact that, unlike OpenVPN, PPTP is quite easily blocked by firewalls. It compensates with its superior speeds though.
PPTP vs IKEv2/IPSec
PPTP is clearly the least safe one of these two, but PPTP is also the easiest one to set up.
When it comes to stability, both PPTP and IKEv2/IPSec show similar results, even though IKEv2/IPSec comes with the advantage of being a lot better for mobile users.
In terms of speed, PPTP and IKEv2/IPSec are pretty similar. Both scored very well in the speed tests and are great choices for those looking for good internet speeds.
PPTP vs L2TP/IPSec
The L2TP/IPSec protocol offers better security than PPTP. In this case, IPSec provides additional security features such as 256-bit encryption. It is almost just as compatible as PPTP, being available on Windows, iOS, Mac, and Android.
Speed is the only thing keeping the comparison between PPTP and L2TP/IPSec worthy of our attention. Since the encryption on PPTP is quite basic when compared with L2TP/IPSec, PPTP offers a much better browsing experience for those in a hurry.
PPTP vs SoftEther
While PPTP is a clear winner when it comes to compatibility, availability, and setup difficulty, it’s important to know that SoftEther leaves PPTP in a cloud of dust in speed and security comparisons.
Even though SoftEther isn’t natively supported by any operating systems at the moment, we believe it’s worth the hassle of installing additional software to use it, rather than going for the PPTP option which is slower and less secure.
PPTP vs SSTP
While PPTP is notorious for the questionable level of security it offers, SSTP supports 256-bit encryption, which makes it a clear winner in this aspect. SSTP is also more effective in avoiding firewall blocks because it operates on the HTTPS port 443.
When it comes to speed, however, PPTP is the one that shines. The same goes for compatibility since SSTP is only natively available on Windows devices.
Bottom line
While many consider PPTP to be outdated and barely secure, there are still reasons to use it to this day, mainly its speed and setup ease. While other VPN protocols may offer better performance, PPTP is still used rather widely.
And if you’re looking for a VPN client supporting PPTP because you decided that this is the protocol that suits your needs, perhaps you could check out HideIPVPN.
Our VPN client supports several protocols, including PPTP, it is available on most devices and it has been designed with you, the user, in mind.
The pricing is more than accessible and we take great pride in the level of service and performance we offer. HideIPVPN offers AES-256 encryption, which is probably the most complex level on offer these days.
On top of this, our support team is always available an



