What is a domain fronting attack? [2023]
Last updated on February 15th, 2023 in Privacy
credit TechTalks
Have you ever heard the phrase domain fronting? It’s a tactic used by hackers and cybercriminals to bypass security measures and gain access to sensitive networks or data. But what is a domain fronting attack, and how does it work?
Let’s take a look at this increasingly common type of cyberattack and discuss how to protect yourself from it. We’ll also look at some of the most recent examples of domain fronting attacks, so you can stay aware of the latest threats.
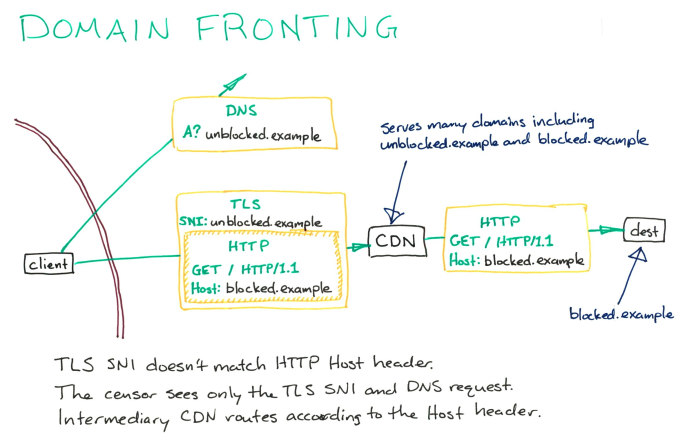
Domain fronting is an attack where an attacker uses a domain that appears to be legitimate to mask their real domain. This can be done by using a subdomain that is similar to the legitimate domain, or by using a URL shortener.
Domain fronting can be used to bypass firewalls and other security measures that are in place to block access to certain websites. It can also be used to evade detection by law enforcement and intelligence agencies.
Domain fronting is a relatively new attack vector, and it is not yet clear how effective it will be in the long term. However, it has already been used in a number of high-profile attacks, and it is likely that we will see more of this type of attack in the future.
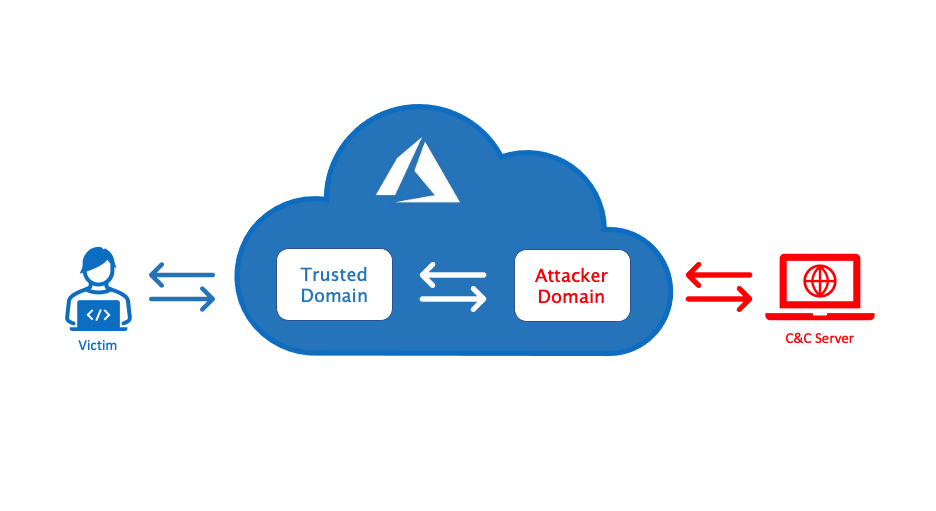 These kinds of attacks take advantage of the fact that many web hosting providers allow multiple domains to be served from a single IP address. This means that an attacker can point their domain to the IP address of a legitimate website, and then host malicious content on a subdomain of that domain.
These kinds of attacks take advantage of the fact that many web hosting providers allow multiple domains to be served from a single IP address. This means that an attacker can point their domain to the IP address of a legitimate website, and then host malicious content on a subdomain of that domain.
When users try to access the malicious content, they are actually accessing the legitimate website, which is then used to serve the content.
This type of attack is often used to circumvent censorship, as it is very difficult for authorities to block all of the domains that could be used for domain fronting. It is also difficult to track down who is responsible for the attack, as the domain name does not resolve to the actual IP address of the server hosting the content.
Domain fronting can also be used for phishing attacks. By pointing their domain to a legitimate website, attackers can make their phishing pages look more credible.
This can trick users into entering their credentials on the fake login page, which can then be used by the attacker.
The main purpose of domain fronting is to access blocked content. It seeks to get around the growing trend of online censorship. For instance, we discovered that 27 countries seemed to tighten censorship in 2022, including Sri Lanka, which outlawed torrenting, restricted the use of some VPNs, and imposed protracted social media control in response to domestic unrest.
Tor further uses it to cloak communications in restricted areas.
The solution was compatible with a number of communication programs that aimed to increase anonymity, including the previously mentioned Signal. Another example is Telegram, while the advocacy group Access Now named a dozen “human rights-enabling technologies” in 2018 (Psiphon, Lantern, Telex (in development), obsf4, ScrambleSuite, meek, meek lite, Collateral Freedom, etc.) that did so.
Penetration tests can be performed via domain fronting. Software like Cobalt Strike, for instance, is used to simulate network attacks. Cobalt Strike has, however, also been utilized by bad actors, as described below.
 What is a domain fronting assault, and how does it appear? Here are a few recent instances of domain fronting assaults.
What is a domain fronting assault, and how does it appear? Here are a few recent instances of domain fronting assaults.
Russian nation-state attackers APT29 were using domain fronting tactics for stealthy backdoor access to victim environments for at least two years, according to threat intelligence firm Mandiant in 2018.
ATP29 did this by utilizing remote access, the Tor network, and the domain fronting plugin meek. APT29 used the security flaw to extract data after infiltrating the system with malware. Domain fronting gave the impression that ATP29’s traffic was reliable.
In September 2021, Cisco Talos found a hacker utilizing domain fronting with the Cloudflare CDN to reroute a domain held by the Myanmar government to a different server. Regarding how it operated:
When the Cobalt Strike beacon is deployed, it will make a DNS request for a trustworthy domain. It can be housed behind Cloudflare infrastructure and change the HTTPs request header. This will tell the CDN to send traffic to an attacker-controlled server.
Domain fronting is a technique used to circumvent censorship and access blocked content. It works by using a different domain name than the one that is actually being accessed. This fools censors into thinking that the user is accessing a different domain. In reality, they are accessing the same content.
Domain fronting is an effective way to bypass censorship because it uses a technique that is not easily detected or blocked. Censors typically block specific domain names. This way the users can access the same content. They can do it without being detected using a different domain name.
 Domain fronting is an attack where an attacker uses a valid domain to host malicious content. The attacker can then use that domain to redirect traffic to their own site or to a third-party site.
Domain fronting is an attack where an attacker uses a valid domain to host malicious content. The attacker can then use that domain to redirect traffic to their own site or to a third-party site.
This allows the attacker to bypass security measures, such as firewalls, that are in place to block access to known malicious domains.
There are a few ways that you can protect against domain fronting attacks:
– Use a reputable security solution that can block access to known malicious domains.
– Configure your firewall to block access to the IP addresses associated with known these kind of services.
– Keep your software and operating system up to date. This will help close any security vulnerabilities that could be exploited by attackers.
These attacks are a dangerous form of cyber-attack. It utilizes domain names to hide the locations from where the requests originate. The attackers use domains associated with popular websites like Google and Amazon. This makes it difficult for organizations to detect these attacks against their networks.
By understanding how this attack works, businesses can take steps to protect their systems from such malicious activities. Implementing effective security measures is key in protecting your organization against domain-fronting attacks. They are such – DDoS mitigation, web application firewalls, and secure URL filtering.