What is Shadow IT?
Last updated on August 8th, 2022 in General

If you’ve been working in the tech industry for any length of time, you’ve probably heard the term “shadow IT” thrown around. But what exactly is shadow IT? In this article, we’ll take a look at what shadow IT is, why it’s a problem, and how to combat it.
Table of contents
Shadow IT refers to the application and devices that employees use within an organization without the knowledge or approval of the organization’s IT department. It can pose a serious security risk to an organization because the IT department is not aware of or cannot control these devices and applications.
This can be beneficial to an organization, as it allows employees to use the tools they are comfortable with and can be more productive. However, Shadow IT can also be a major security risk, as unauthorized devices and applications may not be secure and could allow attackers to gain access to sensitive data.
Organizations need to be aware of the risks posed by Shadow IT and take steps to mitigate them. Employees should be educated on the risks of using unauthorized devices and applications, and only authorized devices and applications should be allowed on the network.
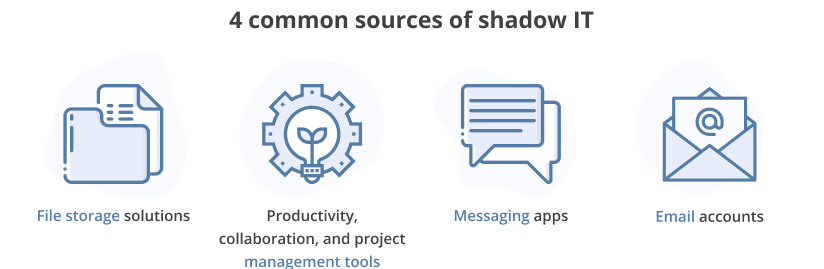
When it comes to shadow IT, there are different types of activities that can fall under this category. Some common examples of shadow IT include using personal devices for work purposes, using unauthorized applications, and accessing unapproved websites. Let’s take a closer look at each of these Shadow IT activities:
One type of Shadow IT activity is using personal devices for work purposes. This can include using a personal laptop or smartphone for work tasks, accessing work email on a personal device, or storing work files on a personal computer. While using personal devices for work can be convenient, it can also pose security risks. For example, if a device is lost or stolen, sensitive company data could be compromised. Additionally, if a personal device is not properly secured, it could be vulnerable to malware and other cyber threats.
Another type of Shadow IT activity is using unauthorized applications. This can include downloading unapproved software, using unauthorized cloud storage services, or accessing unapproved websites. While some employees may view these activities as harmless shortcuts, they can actually pose significant risks to an organization. For example, unauthorized software may not be properly secured and could contain malware.
 There are both pros and cons to using shadow IT within an organization. On the positive side, shadow IT can lead to increased innovation and creativity as employees are free to explore new technologies and ideas without having to go through formal channels. This can lead to improved efficiency and productivity as employees are able to quickly adopt new tools that help them do their jobs better.
There are both pros and cons to using shadow IT within an organization. On the positive side, shadow IT can lead to increased innovation and creativity as employees are free to explore new technologies and ideas without having to go through formal channels. This can lead to improved efficiency and productivity as employees are able to quickly adopt new tools that help them do their jobs better.
On the downside, shadow IT can create security risks as unauthorized applications may not be properly vetted for security vulnerabilities. Additionally, shadow IT can lead to data silos as different departments within an organization adopt different applications, making it difficult to share information and data across the company. Lastly, shadow IT can increase costs as different departments purchase their own applications and licenses, instead of leveraging existing ones across the organization.
Overall, there are both pros and cons to using shadow IT. Organizations need to weigh the risks and benefits of allowing shadow IT in order to decide whether it is right for them.
If your organization is like most, then you probably have some sort of shadow IT lurking in your network. Shadow IT refers to any unauthorized or unapproved technology or services that are being used within an organization. This can include everything from personal devices and apps to cloud-based services. While shadow IT can pose some risks, there are also some potential benefits that should be considered.
If you’re looking to implement shadow IT within your organization, there are a few things you need to keep in mind. First, you need to make sure that all employees are aware of the policies and procedures surrounding shadow IT. This includes specifying what types of devices and services are allowed, and making sure that everyone understands the risks involved. Next, you’ll need to put in place some controls to manage and monitor shadow IT usage. Finally, you should create a process for approving new devices and services for use within the organization.
By taking these steps, you can help ensure that shadow IT is used safely and effectively within your organization.
 Shadow IT is a term used to describe the unauthorized use of technology within an organization. This can include everything from using personal devices for work purposes to downloading unapproved software. While there are some benefits to Shadow IT, it can also pose a number of risks to an organization.
Shadow IT is a term used to describe the unauthorized use of technology within an organization. This can include everything from using personal devices for work purposes to downloading unapproved software. While there are some benefits to Shadow IT, it can also pose a number of risks to an organization.
One of the biggest risks of Shadow IT is that it can lead to data breaches. When employees use unapproved software or devices, they may not be following proper security protocols. This can leave the door open for hackers to gain access to sensitive data. Additionally, Shadow IT can also lead to compliance issues. If an organization is subject to regulations like HIPAA or Sarbanes-Oxley, using unapproved software could put them at risk of violating these rules.
Another risk of Shadow IT is that it can create silos within an organization. When employees use different software or devices, it can be difficult for them to share information and work together. This can lead to inefficiencies and make it harder for an organization to function as a whole.
Let’s get into some point by point:
Your organization’s IT department has less control and visibility over your proprietary data the more it travels through shadow IT channels. This may result in data loss, failure to implement disaster recovery plans, and security and regulatory non-compliance. Your IT department may have a tougher time responding to IT problems if it lacks visibility into the organization’s data flows.
The likelihood that certain shadow IT resources will play a crucial role in your projects increases the more frequently your firm employs them in day-to-day operations. If you find yourself in that circumstance and need to scale down some of your resources to complete the work, the expense to the organization of continuing to use the service might not be worth it. Software as a service (SaaS) solutions like online storage providers are frequently concerned about this.
It is ineffective to store and use data across various, unreliable silos inside your company. The IT department won’t be able to adequately plan for capacity, system design, security, and performance throughout the company if the enterprise is unaware of its own data flows. Your organization may incur time and financial losses if analysis and reporting become increasingly complex and unreliable.
You run a greater chance of falling victim to various online attacks the more insecure devices you allow access to your network. Through a phishing campaign or an unintentional download, ransomware and other malware that gains access to a device connected to your organization’s network can wreck havoc on your infrastructure and result in crucial data loss.
The hazards posed by shadow IT can have far-reaching repercussions if your firm must adhere to strict compliance rules, like government contractors, for instance. Shadow IT will either push you out of compliance or add more audit points where your business will need to show compliance documentation. Assume a federal contractor who works for an organization saves confidential government information in their own cloud account. For each data point in question, your organization might be compelled to audit, identify, and disclose the nature and impact of that “breach.” Your company may be subject to lawsuits and fines for non-compliance, which are not only expensive but may also harm your reputation, in addition to the potential exposure of sensitive information to cyberattacks.
Overall, Shadow IT can be a big risk for organizations. While it can offer some benefits, the potential risks should be considered before allowing employees to use unapproved technology.
Shadow IT can be a big problem for businesses because it means that employees are using unauthorized applications and devices, which can lead to data breaches and other security issues. However, Shadow IT can also be beneficial because it allows employees to be more productive and use the tools that they are most familiar with. If you want to allow Shadow IT in your business, you need to have strict policies and procedures in place to ensure that your data is protected.