 Have you ever heard of a rainbow table attack? If not, then you’re in for a wild ride. Rainbow tables are one of the most dangerous and efficient hacking techniques out there, allowing attackers to bypass even the strongest passwords with ease.
Have you ever heard of a rainbow table attack? If not, then you’re in for a wild ride. Rainbow tables are one of the most dangerous and efficient hacking techniques out there, allowing attackers to bypass even the strongest passwords with ease.
In this blog post, we’ll be exploring what rainbow tables are and how they work – so buckle up and get ready to learn about one of the scariest cyber threats out there!
What is a rainbow table attack?
A rainbow table attack is a type of cyber attack that uses a database of pre-computed hashes to crack passwords. The attacker first creates a large database of common passwords and their corresponding hashes. They then use this database to look up the hash of the password they are trying to crack.
If the password is in the database, the attacker can quickly determine what it is. Rainbow table attacks are very efficient and can be used to crack even strong passwords.
What is Hashing?
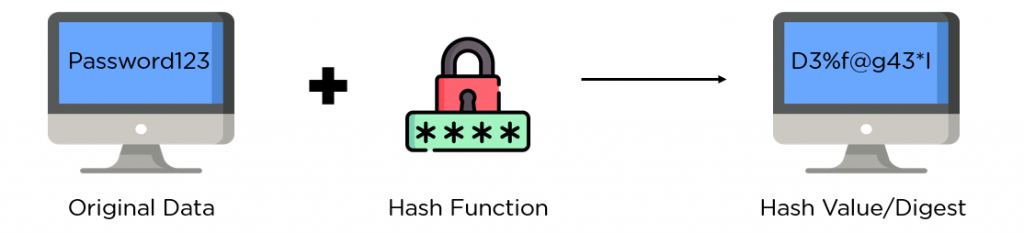 In order to render any given key or string of characters (such as a password or username) illegible and useless to cybercriminals, it must be hashed into a separate string of characters, also known as the hash value. This is accomplished by passing the password via a hash function, a one-way mathematical method. The company’s server then stores hashed passwords.
In order to render any given key or string of characters (such as a password or username) illegible and useless to cybercriminals, it must be hashed into a separate string of characters, also known as the hash value. This is accomplished by passing the password via a hash function, a one-way mathematical method. The company’s server then stores hashed passwords.
An organization can verify the legitimacy of users without storing the actual passwords if it utilizes hashing. The hash value of every password entered by a user is then compared to the hash value kept on the company’s servers.
The user gets authorized and given access if the values line up. Hashing algorithms, however, are also vulnerable to attacks such as the rainbow table attack. But how do they work?
How does a rainbow table attack work?
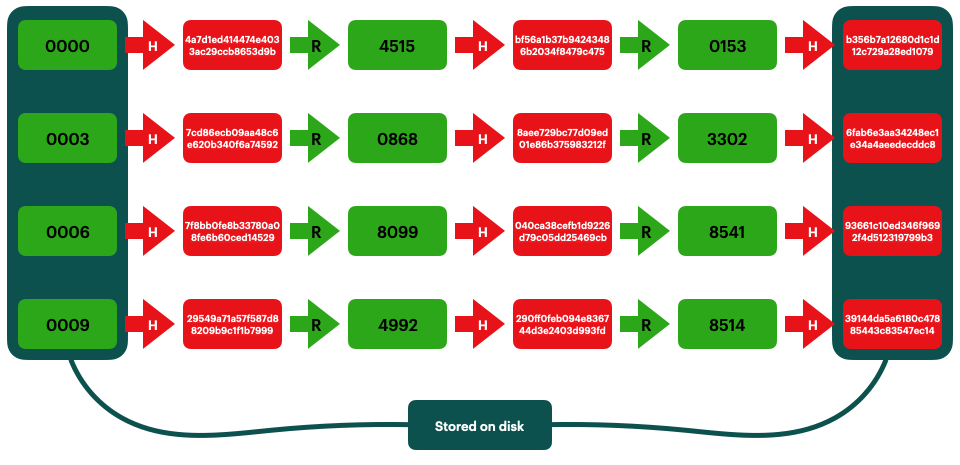
A rainbow table attack is a type of cryptanalytic attack that targets encrypted passwords. The attack is named after the Rainbow Table, a data structure that is used to store large sets of precomputed hashes. The goal of the attacker is to use the rainbow table to crack the encryption on a password, thereby revealing the plaintext password.
Rainbow tables are created by first generating a large set of possible plaintext passwords, and then hashing each password using a cryptographic hash function. The attacker then creates a table that maps each hash back to its corresponding plaintext password.
To carry out an attack, the attacker simply needs to compute the hash of the target password and look up the corresponding plaintext password in the table.
Rainbow tables are most effective against weak passwords that are short and use simple character sets (e.g., “password” or “1234”). Stronger passwords that are longer and use complex character sets (e.g., “P@ssw0rd1”) are much more resistant to rainbow table attacks.
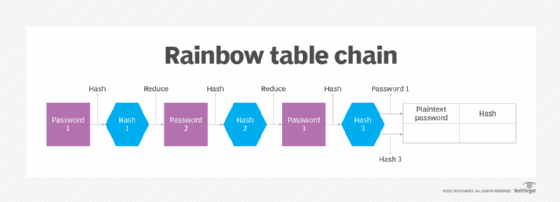
Rainbow table attack steps:
- Generation. The rainbow table begins with a list of potential passwords and uses a hash function to create a list of hashes for each password. The generated hashes are kept in the rainbow table together with the accompanying plaintext passwords.
- Reduction. To create a new set of hashes, the hashes in the rainbow table are further processed using a reduction function. Each hash is converted to a new value via the reduction function, which serves as the foundation for the following phase. To create a chain of hashes, this procedure is performed numerous times.
- Lookup. A hacker can utilize the rainbow table to identify the associated plaintext passwords when they have a collection of hashes. The hashes in the rainbow table are reverse-looked up by starting with the final hash in each chain and moving backward through the hashing order until they come upon a match with the target hash.
- Cracking. When a corresponding hash value is discovered, it signifies that the target hash’s original plaintext password is the one that corresponds. The hacker can now access someone else’s account by abusing the authentication process.
Why are rainbow table attacks becoming more common?
Rainbow table attacks are becoming more common for a number of reasons. First, as computer hardware becomes more powerful, the time it takes to crack encryption using rainbow tables is decreased.
Second, the availability of rainbow tables has increased, as they can be easily found online.
Finally, many people still use weak passwords that can be easily cracked using rainbow tables.
How can you protect yourself from a rainbow table attack?
One way to protect yourself from a rainbow table attack is to use a strong password that is not found in any known rainbow table. Another way to protect yourself is to use a one-time pad, which is a key that is used only once and then destroyed.
Use VPN to protect against attacks
A VPN, or virtual private network, can help protect your online privacy by creating a secure, encrypted connection between your device and a server. This can prevent third parties from snooping on your traffic or intercepting your data. A VPN can also help improve your security if you’re using public Wi-Fi, as it will encrypt your traffic and prevent others from being able to see what you’re doing.
There are many different types of VPNs available, so it’s important to choose one that’s right for you.
Some factors to consider include the level of security offered, the speed of the connection, and whether the VPN allows you to access geo-blocked content.
If you’re looking for a VPN to protect against rainbow table attacks specifically, make sure to choose one with robust security features such as military-grade encryption.
Best VPN to protect against attacks
HideIPVPN offers a VPN service with military-grade encryption, and high-speed servers with unlimited bandwidth.
Our service comes with shared IP addresses so that your activity can never be tied to one particular user, further protecting your privacy.
We also offer DNS leak protection, a Kill Switch, the latest VPN protocols, and a guaranteed no-log policy.
Best VPN Deal! Get HideIPVPN for $2.7/mo!
Every purchase you make comes with a 30-day money-back guarantee.
Conclusion
A rainbow table attack is a sophisticated technique used to crack passwords by taking advantage of the weaknesses in hashing algorithms. By pre-computing and storing large tables of hashes, it can quickly reverse hash a plaintext password, making it easier for attackers to gain access to confidential information.
It’s important that organizations take steps to secure their systems against this type of attack by using stronger hashing algorithms and longer passwords. With these precautions in place, they’ll be better protected from the potential risks posed by rainbow table attacks.



