What is a Collision Attack? [2022]
Last updated on September 5th, 2022 in Privacy
 In cryptography, a collision attack is an attack that finds two different input values that produce the same output value. This can be used to create a forged signature or to break a hash function.
In cryptography, a collision attack is an attack that finds two different input values that produce the same output value. This can be used to create a forged signature or to break a hash function.
A collision attack is a type of cyber attack that seeks to exploit vulnerabilities in a system by causing two different inputs to produce the same output. This can be done, for example, by causing two different pieces of data to hash to the same value. Collision attacks can be used to launch a variety of other attacks, such as denial-of-service attacks or malware propagation.
When things don’t go as expected and two distinct inputs actually produce the same hash value, this is called a collision. Although this shouldn’t happen, it might be very troublesome if it does. Attackers can fully compromise the integrity and authentication features of digital signatures when collisions are feasible. This can result in a variety of issues, including fraud and giving attackers a way to get around current security measures.
Here’s a little secret: It’s actually not possible to create a hash function that entirely prevents collisions.
The pigeonhole theory is to blame for this. It basically states that some inputs must produce the same hashes if there are more inputs than there are potential hashes in the context of hashing. SHA-256 uses hashes that are 256 bits long.
This indicates that there is a maximum size for an SHA-256 hash, much as there is a maximum value of 999,999 that can be displayed on a car’s odometer if it only has six digits. There are only a certain amount of possible hashes if there is a maximum size for a hash.
A collision attack is a type of cyber attack that seeks to exploit the vulnerabilities of a system by injecting malicious data into it. The goal of a collision attack is to cause the system to malfunction or crash.
One way that attackers can carry out a collision attack is by flooding the target system with requests that overload its capacity. This can cause the system to freeze or crash. Another way to carry out a collision attack is by sending two identical requests to the system. This can confuse the system and cause it to return an error message.
Collision attacks can be very difficult to detect and defend against. However, there are some steps that you can take to protect your system from these types of attacks. For example, you can limit the number of requests that your system accepts from any one IP address. You can also implement security measures such as firewalls and intrusion detection systems.
Below we will list some of the most popular types of collision attacks:
 The Merkle-Damgard construction-based hash functions are susceptible to freestart collision attacks. This indicates that MD5, SHA-1, and SHA-2 are weak points, but not SHA-3, which is built using sponge technology.
The Merkle-Damgard construction-based hash functions are susceptible to freestart collision attacks. This indicates that MD5, SHA-1, and SHA-2 are weak points, but not SHA-3, which is built using sponge technology.
In the first round of a Merkle-Damgard hash function, a set of specified initialization vectors and the first block of message data are typically the inputs. If you want to learn more about the fundamentals of hash functions, you might want to read this essay on the MD5 algorithm.
In contrast, a freestart collision involves giving the attacker the freedom to select their own initialization vectors. They are able to lower the hash function’s security in this way.
Since an attacker cannot actually choose the initialization vectors, these aren’t actual attacks on the implementation of a secure hash function. However, they are crucial for understanding the drawbacks of a specific hash function and for the future development of more effective cryptographic hash functions.
The likelihood of a successful collision attack depends on the cryptographic hash function’s potential vulnerabilities as well as the size of the hash. Birthday assaults are more dangerous than brute force attacks since they require an attacker to systematically search through every possible combination until they identify a collision, even if a hash function has no known vulnerabilities.
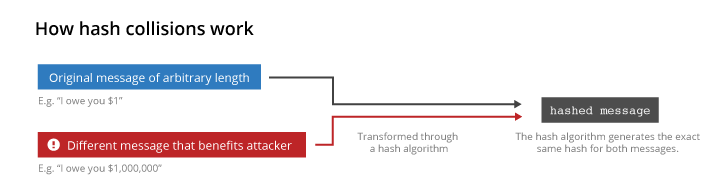
A collision attack locates two distinct messages, m1 and m2, such that hash(m1) = hash, mathematically speaking (m2). In a traditional collision attack, neither message’s content is under the attacker’s control; instead, the algorithm randomly selects them.
Every cryptographic hash function is intrinsically vulnerable to collisions using a birthday attack, just like symmetric-key ciphers are subject to brute force attacks. These attacks are substantially quicker than a brute force attack would be because of the birthday problem.
Another kind of collision attack that Merkle-Damgard hash algorithms are susceptible to is chosen-prefix collision. They are substantially more difficult, but when they are feasible, they offer a much bigger threat than traditional collision attacks.
A chosen-prefix collision includes more restrictions than the traditional collision assaults that we discussed earlier. The attacker must be able to identify collisions using two predefined prefixes rather than simply being able to detect any collisions.
In essence, the attacker is handed two different strings of data in the form of two message prefixes. The next task for the adversary is to locate a unique message for every prefix, even though both the prefix and message combinations share the same hash. We won’t lie; if you’re not into cryptography, this might be a little difficult to understand.
 Preimage attacks are similar to collision attacks in that they search for messages that produce particular hashes. You need merely be aware that: We shall go into these in greater detail in a later article.
Preimage attacks are similar to collision attacks in that they search for messages that produce particular hashes. You need merely be aware that: We shall go into these in greater detail in a later article.
1. A preimage attack entails determining the original input that led to a specific hash after using it as a starting point.
2. A second preimage attack entails taking the input that has been provided and looking for another input that produces the same hash.
The most recent Secure Hash Algorithm is SHA-3. Since SHA-2 is still regarded as secure, there isn’t much purpose in making the effort to switch over at this time, hence we don’t see SHA-3 deployed very frequently.
It is not necessarily more secure than SHA-2 despite being newer. Due to its relative youth and drastically differing internal designs, SHA-3 hasn’t received as much research as SHA-2. We actually don’t know which algorithm will withstand the test of time, therefore it’s preferable to think of it as a spare rather than an upgrade to SHA-2.
Now that you are aware of SHA-3’s function, let’s look at some of the most effective defenses against it. The algorithm that would become SHA-3 had collisions in up to five rounds, according to a 2012 article that was released. The Keccak algorithm was targeted by the researchers using generalized internal differentials.
The researchers detected collisions for three-round versions of both Keccak-384 and Keccak-512. Additionally, they discovered an attack that outperformed a birthday attack against Keccak-384 by 245 times. They were successful in finding collisions for five rounds against Keccak-256. These attempts, meanwhile, were by no means a threat to the algorithms, each of which has 24 cycles.
SHA-2 is currently considered the gold standard in cryptographic algorithms, and it’s implemented broadly across our digital world.
You should be able to infer that collisions haven’t done much damage to it at this point because it’s still regarded as secure. We would all need to be very concerned about our online security if classical collisions or chosen-prefix collisions had been discovered.
Although it is still regarded as secure, cryptographers have been working hard to crack it. Due to its 256-bit size, the SHA-256 algorithm has 128 bits of security against birthday attacks. SHA-512 has 256 bits of security against birthday attacks thanks to its doubled bit length.
Collisions versus SHA-2 are not a significant concern at this time. But it’s still essential that academics keep studying SHA-2 and hunting for flaws. If they don’t, nation states and organized crime will still do it and won’t let us know when they discover collisions that make sense.
There are many benefits to implementing a collision attack as part of your cybersecurity strategy. A collision attack can help you to:
-Identify and exploit weaknesses in hashing algorithms
-Generate hashes for known data to compare against hashes of unknown data (for example, to crack passwords)
-Generate two pieces of data that hash to the same value (known as a “collision”)
Collision attacks can be used for both good and evil. They can be used to find vulnerabilities in systems or to crack passwords. However, they can also be used by attackers to create false data or to impersonate someone else.
Overall, collision attacks can be a powerful tool in your cybersecurity arsenal. Used correctly, they can help you to find and exploit weaknesses in systems. But be aware of the potential risks involved in using them.
There are a few disadvantages to using a collision attack. First, it can be difficult to find two pieces of data that collide. Second, even if you do find two pieces of data that collide, the resulting hash may not be very useful. Finally, collision attacks can be computationally expensive.

A collision attack is a type of attack on a cryptographic hash function that uses two different inputs that produce the same hash output. This type of attack can be used to find vulnerabilities in a system or to forge signatures. Collision attacks are a major threat to cryptographic hash functions, and they can be very difficult to prevent.
One way to prevent a collision attack is to use a cryptographically secure hash function. A cryptographically secure hash function is a function that is designed to make it difficult for an attacker to find two inputs that produce the same hash output. Cryptographically secure hash functions are often used in cryptographic systems, such as digital signatures and message authentication codes.
Another way to prevent a collision attack is to use a salt. A salt is a random string of data that is used as an additional input to a hash function. Salts are often used in password hashing algorithms, such as bcrypt and PBKDF2. Adding salt to the input of a hash function makes it much more difficult for an attacker to find two inputs that produce the same hash output.
If you are using a cryptographic system that is vulnerable to collision attacks, you should update it to use a more secure hashing algorithm. You should
In conclusion, a collision attack is a form of cryptography attack that exploits the fact that some hash functions can produce the same output for two different inputs. This type of attack can be used to impersonate another person or entity, or to forge digital signatures. While collision attacks are not common, they can be difficult to detect and prevent. As such, it is important for businesses and individuals to be aware of this type of attack and take steps to protect themselves from it.