What is Sha Encryption? [2022]
Last updated on July 11th, 2022 in VPN
If you’ve ever wondered how your data is protected when it’s transmitted across the internet, you’re not alone. Sha encryption is a technique that is used to ensure that data is securely transmitted between two parties. In this article, we’ll take a closer look at what is sha encryption and how it works.
Table of contents
Sha encryption is a type of encryption that is used to protect information. Sha stands for Secure Hash Algorithm. Sha encryption is a form of public key cryptography, which means that it uses two keys to encrypt and decrypt data. One of these keys is public and the other is private. The public key can be known by anyone, but the private key must be kept secret. Sha encryption is used in many different applications, such as email, file sharing, and secure communications.
Hashing is a process of converting a given input into a fixed-size alphanumeric string. The input can be of any size, but the output will always be of the same length. Hashing is commonly used to store passwords in databases. When a user enters their password, the hash of the password is stored in the database instead of the actual password. This makes it more difficult for someone to steal passwords from a database.
Sha Encryption is a type of hashing algorithm that is used to encrypt data. It is is more secure than other types of hashing algorithms. This is because Sha Encryption uses a longer key length. This makes it more difficult for someone to guess the key and decrypt the data.
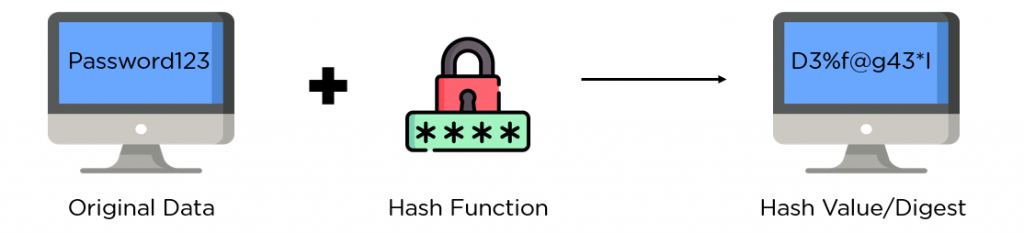
via Simplilearn
There are three different types of SHA encryption: SHA-1, SHA-2, and SHA-3.
This is the most common type of SHA encryption. It was developed by the US National Security Agency in 1995.
The Secure Hash Algorithm (SHA) family consists of four algorithms, SHA-1 being just one of them. Most were created by the National Institute of Standards and Technology (NIST) and published by the US National Security Agency (NSA) (NIST).
The second version of this cryptographic hash function is called SHA-1. This one also features a 160-bit message digest and aimed to improve security by addressing a SHA-0 flaw. But SHA-1 was also discovered to be unsafe in 2005.
After SHA-1’s cryptographic flaws were discovered, NIST issued a statement in 2006 urging federal entities to switch to SHA-2 by the year 2010. Since SHA-2 is more robust than SHA-1, assaults against it are unlikely to succeed given the state of computers.
Companies including Google, Mozilla, and Microsoft, in addition to federal agencies, have either started planning to stop accepting SHA-1 SSL certificates or have already barred access to those types of URLs.
This is a more secure type of SHA encryption. It was developed by the US National Security Agency in 2001.
Many years after SHA-1, SHA-2 was released in 2001. It has six hash functions: SHA-224, SHA-256, SHA-384, SHA-512, SHA-512/224, and SHA-512/256, all of which have different digest widths.
Another member of the Secure Hash Algorithm family, SHA-3, was created by non-NSA designers and disclosed by NIST in 2015. (formerly Keccak).
This is the most recent type of SHA encryption. It was developed by the US National Security Agency in 2015.
SHA-3 (Secure Hash Algorithm Version 3), also known as Keccak, was created in 2008 by a team of authors under the direction of Yoan Dimen and became the new FIPS standard in 2015. It is a unidirectional function for creating digital prints of the chosen length (the standard accepts 224, 256, 384, or 512 bits) from input data of any size. The mixing function and compression to the chosen size “cryptographic sponge” are how the algorithm operates.
The size of the data block, the size of the algorithm state, the number of rounds in the f function, and other variables are all customizable in the original Keccak algorithm in order to give the best balance between cryptographic stability and performance for use on the chosen platform. The updated SHA-3 algorithm differs from the original in a number of ways.
There are a few different types of encryption, but SHA is one of the most common. It’s also one of the most secure, which is why it’s often used for things like financial transactions. But SHA encryption isn’t perfect, and there are a few potential downsides to using it.
One potential downside is that SHA encryption is slower than some other types of encryption. This can be a problem if you’re encrypting large amounts of data or if you need real-time encryption.
Another potential downside is that SHA encryption is less flexible than some other types of encryption. This means that it can be more difficult to change your encryption keys or algorithms if you need to.
Overall, SHA encryption is a very strong form of encryption that is suitable for most purposes. However, it’s important to understand the potential downsides before you use it.
With the development of a cheap “chosen-prefix collision attack,” a more useful variation of the SHA-1 collision attack initially used by Google two years ago, attacks on the SHA-1 hashing algorithm have suddenly become far more serious.
This means that SHA-1 collision attacks may now be conducted with arbitrary inputs and are no longer limited to unintentional errors, enabling attackers to target specific files for copying and faking.
Although the SHA-1 hashing function was potentially compromised in 2005, the first real-world effective collision attack only occurred in 2017.
Also in 2017, researchers from Google and CWI created two files with the exact same SHA-1 hash in what is known as the “SHAttered” assault, the first-ever SHA-1 collision.
Cryptographers projected that SHA-1 would be broken in a practical setting, however, the SHAttered study arrived three years faster than anticipated and cost only $110,000 to implement utilizing cloud computing resources, significantly less than anticipated.
SHA-256, developed in 2001, has a 50% chance of surviving a birthday attack and 128-bit generic collision resistance. The 128-bit is difficult to access. The Bitcoin miners are a well-known example, as they can generate 292 double SHA-256 hashes annually as a group (it is almost 293 after two years). Therefore, it will take 236 years to locate a collision with a 50% chance.
On the other hand, SHA-512 offers 256-bit generic collision resistance. 256 bit is impervious.
The general collision resistance of SHA-3-512 is the same as that of SHA-512. The key distinctions are that the SHA-2 series has MD construction and lacks length-extension resistance if not trimmed, whereas the SHA-3 series uses sponge construction and possesses resistance to length-extension attack.
There are a few different types of Sha encryption, but the most secure is Sha-256. This type of encryption is often used by financial institutions and other organizations that handle sensitive information.
One of the SHA-2 hash functions that replace SHA-1 is SHA-256, which is among the most powerful ones now in use. SHA-256 is not significantly more difficult to code than SHA-1 and is currently uncompromised.
It works well as an AES companion function because of the 256-bit key. It is described in the FIPS 180-4 standard published by the National Institute of Standards and Technology (NIST). NIST also offers a variety of test vectors to confirm the accuracy of implementation.
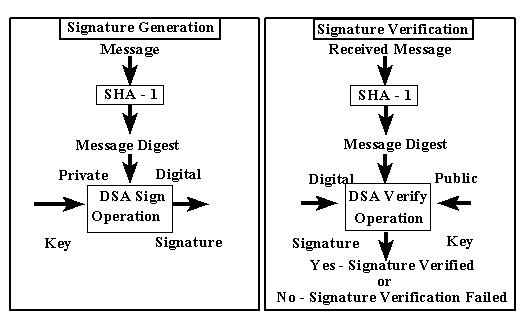
via temple.edu
Sha encryption is a process of encrypting data that is used to protect information. This process is used to scramble data so that it cannot be read by anyone who does not have the proper key to decrypt it. Sha encryption is a very secure way to protect data, and is often used by businesses and governments to protect sensitive information.
There are a number of alternative encryption methods to Sha, including:
-AES encryption: AES is a symmetric key algorithm that is widely used for encrypting data.
-Blowfish encryption: Blowfish is a symmetric key algorithm that is designed for fast encryption.
-DES encryption: DES is a symmetric key algorithm that was once the standard for data encryption.
A SHA1 hash is typically only utilized for an hour in your VPN tunnel before being replaced by a fresh key. A packet that has already been encrypted is verified using the hash technique. As a result, an attacker could only use this method to secretly insert a phony packet into your data, and they would need to do so within an hour.
Since the encryption process effectively creates two layers of security, it would still be difficult for someone to access your data.
Today’s VPN services accept SHA-2 hashes (e.g. SHA-256, SHA-384, or SHA-512). These are unbreakable, extremely secure SHA variations. Many well-known VPN vendors, like HideIPVPN, have SHA-2 supported and set as the default option.
HideIPVPN offers a VPN service with military-grade encryption, and high-speed servers with unlimited bandwidth.
Our service comes with shared IP addresses so that your activity can never be tied to one particular user, further protecting your privacy.
We also offer DNS leak protection, a Kill Switch, the latest VPN protocols, and a guaranteed no-log policy.
Every purchase you make comes with a 30-day money-back guarantee.
Sha encryption is a type of encryption that is used to protect data. Sha encryption is a strong form of encryption that is difficult to break. Sha encryption is used by many organizations to protect their data.