 Are you worried about cyber threats? As technology advances, so do the methods of hacking and malware spread. One of the most dangerous types of malware is a remote access trojan or RAT.
Are you worried about cyber threats? As technology advances, so do the methods of hacking and malware spread. One of the most dangerous types of malware is a remote access trojan or RAT.
In this blog post, we will discuss everything you need to know about remote access trojans in 2023 – how they work, how they can harm your device, and what measures you can take to protect yourself from them.
So get ready to learn more about one of the biggest cybersecurity risks out there!
What is a remote access trojan?
A remote access Trojan (RAT) is a type of malware that allows hackers to control a victim’s device remotely. RATs are often used to steal personal information, such as login credentials and credit card numbers. They can also be used to install other types of malware on a victim’s device.
RATs are usually spread through phishing emails or malicious websites. Once a victim clicks on a malicious link or opens a malicious attachment, the RAT is installed on their device. Hackers can then use the RAT to gain access to the victim’s device and files.
RATs can be difficult to detect because they masquerade as legitimate programs or files. They may also use encryption to avoid detection by security software. If you suspect that your device has been infected with a RAT, you should run a security scan as soon as possible.
How do remote access trojans work?
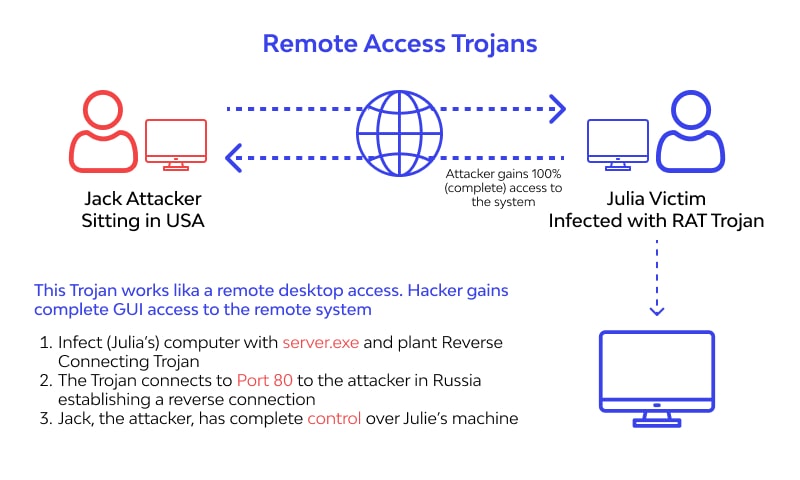
via Wallarm
Remote access trojans are malicious software that allows attackers to gain control of a victim’s computer. The attacker can then use the victim’s machine to carry out attacks on other computers, install additional malware, or steal sensitive data.
There are many different ways that remote access trojans can work, but they all ultimately allow the attacker to take over the victim’s machine and use it for their own purposes.
One common way that these trojans work is by installing a backdoor on the victim’s computer. This backdoor gives the attacker access to the machine even if the user has changed their password or taken other security measures.
Another common method is to use a phishing attack to trick the user into downloading and running the trojan.
Once installed, remote access trojans can be very difficult to detect and remove. They often masquerade as legitimate programs or system files, making them hard to spot even for experienced users.
If you think your computer may be infected with a remote access trojan, it is important to run a security scan with an antivirus program as soon as possible.
What are the dangers of a remote access trojan?
A remote access trojan (RAT) is a type of malware that gives an attacker control over a victim’s device. RATs are often used to spy on victims, steal personal information, or even take control of the victim’s device.
RATs can be extremely dangerous because they give attackers complete control over the victim’s device. An attacker could use a RAT to spy on the victim, steal personal information, or even take control of the victim’s device. RATs can also be used to spread other malware to the victim’s device or network.
There are many different ways that RATs can be installed on a victim’s device. The most common method is phishing emails or malicious websites.
Once the RAT is installed, it will usually connect back to the attacker’s server in order to receive instructions.
Attackers can use RATs to do almost anything they want with the victim’s device. However, some of the most common uses for RATs include:
-Stealing personal information such as passwords, banking information, and credit card numbers
-Spying on the victim by monitoring their activity and conversations
-Taking control of the victim’s device in order to use it for attacks against other devices or networks
RATs can be very difficult to detect and remove once they have been installed on a victim’s device. If you think your device may have been infected with a RAT, it
How to protect against remote access trojans
 In order to protect against remote access trojans, it is essential to understand what they are and how they work. A remote access trojan (RAT) is a type of malware that allows attackers to gain control of a victim’s computer remotely.
In order to protect against remote access trojans, it is essential to understand what they are and how they work. A remote access trojan (RAT) is a type of malware that allows attackers to gain control of a victim’s computer remotely.
RATs are often used to steal sensitive information or to install other forms of malware on the victim’s machine.
There are a few ways to protect against RATs:
1. Use a trusted anti-malware program: Anti-malware programs can detect and remove RATs from your computer. Be sure to keep your anti-malware program up-to-date with the latest virus definitions in order to maximize protection.
2. Be cautious when downloading files: Only download files from trusted sources. If you’re unsure about a file, scan it with an anti-malware program before opening it.
3. Don’t click on links in email or instant messages: Many RATs are spread through malicious links that are sent via email or instant messages. If you receive a link from an unknown source, do not click on it.
4. Keep your operating system and software up-to-date: Attackers often exploit vulnerabilities in outdated software to install RATs on victims’ computers. Make sure you have the latest security updates installed for your operating system and all the software you use.
VPN to protect against Trojans
A remote access trojan (RAT) is a type of malware that allows an attacker to gain control of a victim’s computer. RATs are often used to steal sensitive information or to install other types of malware on the victim’s computer.
Using a Virtual Private Network (VPN) is a great way to protect yourself against Trojans and other types of malicious software. Trojans are a type of malware that can infect your computer and steal your personal information, such as passwords and credit card numbers. VPNs can help protect against Trojans by encrypting your internet connection and hiding your IP address, making it more difficult for attackers to access your computer.
Here are some steps you can take to use a VPN to protect against Trojans:
- Choose a reputable VPN service: Not all VPN services are created equal. Look for a VPN service that has a good reputation for security and privacy. Read reviews and do your research before choosing a VPN service.
- Install the VPN software: Once you have chosen a VPN service, download and install the software on your computer. Follow the instructions provided by the VPN service to set up the software.
- Connect to the VPN server: Once the VPN software is installed, connect to a VPN server. This will encrypt your internet connection and hide your IP address.
- Browse the internet safely: With your VPN connection established, you can now browse the internet safely. Trojans and other types of malware will find it more difficult to infect your computer because your internet connection is encrypted and your IP address is hidden.
- Keep your VPN software up to date: VPN software can occasionally have security vulnerabilities that need to be patched. Make sure you keep your VPN software up to date to stay protected against Trojans and other types of malware.
In addition to using a VPN, it’s also important to practice safe internet habits. Avoid clicking on suspicious links or downloading files from untrusted sources. Keep your operating system and other software up to date with the latest security patches.
By taking these steps, you can protect yourself against Trojans and other types of malware.
Best VPN to protect against Trojans
HideIPVPN offers a VPN service with military-grade encryption, and high-speed servers with unlimited bandwidth.
Our service comes with shared IP addresses so that your activity can never be tied to one particular user, further protecting your privacy.
We also offer DNS leak protection, a Kill Switch, the latest VPN protocols, and a guaranteed no-log policy.
Best VPN Deal! Get HideIPVPN for $2.7/mo!
Every purchase you make comes with a 30-day money-back guarantee.
Conclusion
Remote access trojans are malicious software that can be used to gain unauthorized access and control over computers.
As cyber threats continue to evolve, it is important for computer users to stay informed about RATs so they know how to detect, prevent, and protect against them.
By investing in reliable security tools and maintaining best practices when using the internet, you can help keep yourself safe from remote access trojan attacks.



