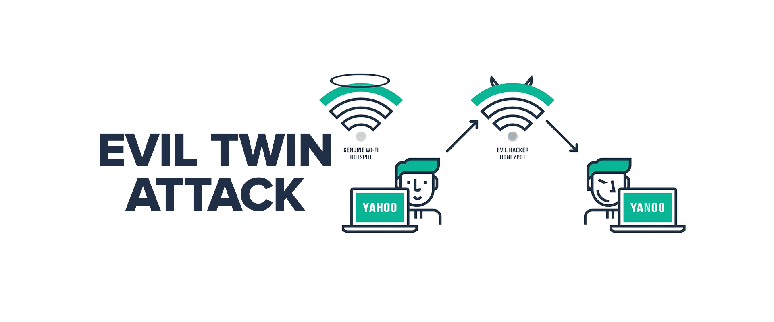
 While most people are familiar with the concept of a “mirror image”, not as many are aware of the term “evil twin”. An evil twin is a malicious replica of a legitimate wireless access point. These twins are often used to carry out attacks on unsuspecting victims by eavesdropping on their communications or redirecting them to fake websites. In this article, we’ll take a closer look at evil twin attacks and how you can protect yourself from them.
While most people are familiar with the concept of a “mirror image”, not as many are aware of the term “evil twin”. An evil twin is a malicious replica of a legitimate wireless access point. These twins are often used to carry out attacks on unsuspecting victims by eavesdropping on their communications or redirecting them to fake websites. In this article, we’ll take a closer look at evil twin attacks and how you can protect yourself from them.
Table of contents
What is an evil twin attack?
An evil twin is a type of cyberattack where an attacker creates a duplicate of a legitimate Wi-Fi network and entices users to connect to it. Once connected, the attacker can steal sensitive data or infect the devices with malware. Evil twin attacks are becoming more common as Wi-Fi networks become more ubiquitous. To protect yourself from an evil twin attack, be sure to only connect to networks that you trust and be suspicious of any unexpected pop-ups or requests for personal information.
When you connect to a fake Wi-Fi network, you run the risk of being attacked by an evil twin. This is a type of cyberattack where a malicious user creates a fake Wi-Fi network that looks and feels like a legitimate network. Once you connect to this network, they can steal your personal information, access your online accounts, or even hijack your computer. If you’re connected to this evil twin network, your network traffic, login credentials, and other sensitive information can be stolen. These networks are nearly impossible to identify because they have the same name and MAC address, making them indistinguishable.
How does an evil twin attack work?
 An evil twin attack is a type of wireless hacking where the attacker creates a fake wireless access point that looks identical to a legitimate one. When users connect to the evil twin, they are actually connecting to the attacker, who can then intercept and steal their data. Evil twin attacks are difficult to defend against because they can be very hard to spot. The best defense is to only connect to known and trusted networks, and to be aware of any suspicious activity on public Wi-Fi networks.
An evil twin attack is a type of wireless hacking where the attacker creates a fake wireless access point that looks identical to a legitimate one. When users connect to the evil twin, they are actually connecting to the attacker, who can then intercept and steal their data. Evil twin attacks are difficult to defend against because they can be very hard to spot. The best defense is to only connect to known and trusted networks, and to be aware of any suspicious activity on public Wi-Fi networks.
An evil twin attack aims to trick users into joining a malicious Wi-Fi network masquerading as a legitimate Wi-Fi network. Hackers take advantage of this usually using by these means:
1. Choose a location with public Wi-Fi. Hackers choose crowded places with free Wi-Fi, such as airports and coffee shops. These locations usually have multiple access points with the same name, making it difficult to detect evil twin networks.
2. Set up a Wi-Fi access point. A hacker creates a new hotspot with his SSID name identical to the legitimate network. Wi-Fi Pineapples (a type of router used by hackers to intercept data) can also be affected.
3. Creation of fake captive portal pages. Before you log into a public Wi-Fi network, you’re usually asked to submit data on a login page called a captive portal. Hackers clone this page to trick users into revealing their login credentials and other sensitive information.
4. Prompt the victim to connect to her WiFi of the Evil Twin. Hackers install evil twin access points near potential victims to create a stronger signal. This encourages victims to connect to the evil twin network through the more vulnerable legitimate network.
5. Collect victim data. Once victims connect to the Evil Twin’s network, hackers can monitor their online behavior. Hackers can collect credentials when a victim logs into her accounts online, such as her social media or banking apps. This gives hackers access to those apps.
Types of evil twin attacks
There are two types of evil twin attacks: the passive attack and the active attack.
In a passive attack, the attacker sets up a rogue access point that masquerades as a legitimate one. When users connect to the rogue access point, they unwittingly reveal sensitive information, such as passwords or credit card numbers.
Active attacks are more sophisticated and dangerous. In an active attack, the attacker not only impersonates a legitimate access point, but also intercepts and modifies data passing between the user and the legitimate access point. This type of attack can be used to inject malware onto a user’s device or to redirect them to a malicious website.
Defenses against evil twin attacks
An evil twin attack is a serious threat to the security of your home or office network. However, there are some things you can do to defend against this type of attack.
First, make sure that your wireless router is properly configured. Enable security features such as encryption and password protection. This will help to prevent unauthorized access to your network.
Second, be aware of the devices that are connected to your network. If you see any suspicious activity, disconnect the device immediately.
Finally, keep your antivirus and anti-spyware software up to date. These programs can help to detect and remove malicious software from your system.
Other ways to avoid an evil twin attack:
- Avoid WiFi networks marked as unsafe. These networks lack basic security features and the data transmitted is unprotected and unencrypted. Evil twin networks usually have this designation.
- Disable automatic Wi-Fi saving. If you’ve previously connected to a malicious network, Autosave Wi-Fi will reconnect to the network the next time it’s in range, exposing you to another attack. Set your device to ask for permission before connecting to the network.
- Browse to HTTPS sites only. If you need to use public WiFi, please visit the HTTPS website. The HTTPS website features end-to-end encryption to prevent hackers from seeing his website activity. These sites are more secure than regular HTTP sites and have a padlock icon next to the URL.
- Set up two-factor authentication for your account. Even if a hacker had access to your account’s username and password, it wouldn’t be easy if you set up two-factor authentication.
How Does a VPN Help with Evil Twin Attacks?
An evil twin attack is a type of Wi-Fi spoofing attack that tricks users into connecting to a malicious Wi-Fi network. This can happen if an attacker sets up a fake Wi-Fi network that has the same name as a legitimate Wi-Fi network. When users try to connect to the legitimate Wi-Fi network, they may accidentally connect to the fake one instead.
If you’re using a VPN, your data will be encrypted and sent through a secure tunnel to the VPN server. This means that even if you do connect to a malicious Wi-Fi network, your data will still be protected. A VPN can also help you avoid connecting to fake Wi-Fi networks in the first place by verifying the identity of the VPN server before you connect.
Best VPN for Evil Twin
HideIPVPN offers a VPN service with military-grade encryption, and high-speed servers with unlimited bandwidth.
Our service comes with shared IP addresses so that your activity can never be tied to one particular user, further protecting your privacy.
We also offer DNS leak protection, a Kill Switch, the latest VPN protocols, and a guaranteed no-log policy.
Best VPN Deal! Get HideIPVPN for $2.7/mo!
Every purchase you make comes with a 30-day money-back guarantee.
Conclusion
An evil twin attack is a type of wireless security attack in which an attacker creates a clone of a legitimate wireless network and uses it to trick users into connecting to it. This can allow the attacker to intercept sensitive data, such as passwords or credit card numbers. Evil twin attacks are relatively easy to carry out and can be difficult for users to detect, so it’s important to be aware of them and take steps to protect yourself from them.



