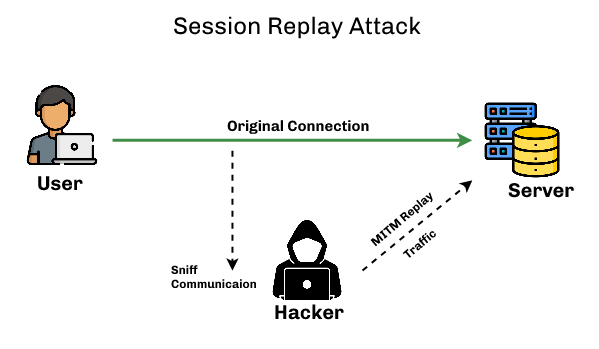
via GeeksforGeeks
A replay attack is a type of attack in which an attacker captures and retransmits a valid data transmission in order to disrupt the communication between two parties or to gain unauthorized access to a system.
Replay attacks are possible because many protocols do not protect against them. For example, the Transmission Control Protocol (TCP) does not have any mechanism to prevent replay attacks, which means that they are possible against any system that uses TCP.
There are two main types of replay attacks:
- Session hijacking: In a session hijacking attack, an attacker eavesdrops on a communication session between two parties and steals the session ID.The attacker can then use the stolen session ID to impersonate one of the parties and gain access to sensitive information or perform actions on behalf of the victim.
- Man-in-the-middle: In a man-in-the-middle attack, an attacker intercepts messages between two parties and modifies them without the knowledge of either party.
The attacker can use this technique to impersonate one of the parties, eavesdrop on the conversation, or redirect traffic to a malicious website.
What is a replay attack?
A replay attack is a type of network attack in which an attacker captures and retransmits data packets in order to disrupt communication or deceive a system. This type of attack can be difficult to detect because the attacker’s activity appears legitimate.
Replay attacks are often used to impersonate a user or device, hijack a session, or bypass security measures.
For e.g. attackers copied transactions on both the ETHPoW and Ethereum chains in September 2022, resulting in a replay assault against the ETHPoW network, which allowed them to take 200 ETHW in total.
Before this, a weakness in Linden Lab’s software (CVE-2007-4961) allowed attackers to record password hashes and repeat them to the Second Life authentication server to get access.
Replay attacks have been found to work against even Tor. Attackers can copy and send a packet by controlling an entry and exit onion router. The packet is rejected as a duplicate when it reaches the exit router, which is now compromised. This, however, disproves the connection’s purported anonymity by revealing to the attacker both the message’s source and its intended recipient.
How do replay attacks work?
 When a hacker replays a captured packet, the receiving system may not be able to tell that the packet is a replay. This is because replayed packets often look identical to normal packets. As a result, the receiving system may process the replayed packet as if it were a normal packet.
When a hacker replays a captured packet, the receiving system may not be able to tell that the packet is a replay. This is because replayed packets often look identical to normal packets. As a result, the receiving system may process the replayed packet as if it were a normal packet.
This can cause problems if the replayed packet contains malicious code. For example, if a hacker replays a captured packet that contains code to delete files from a computer, the receiving system may process the code and delete files.
Replay attacks can be difficult to detect because they often involve normal packets. However, there are some methods that can be used to detect replay attacks. For example, systems can keep track of the order in which they receive packets.
If a system receives a packet out of order, it may be due to a replay attack.
What other methods can attackers use to intercept data?
A type of cyberattack called ARP poisoning leverages flaws in the Address Resolution Protocol (ARP) to reroute network traffic. It only works with networks that employ ARP, however, it can be used to gather data initially for a replay attack.
ARP is made to translate between IP addresses and Media Access Control (MAC) addresses (at the data link layer) (at the network layer). It enables networked devices to discover which devices have specific IP addresses.
The outcomes are kept, and a list of the most recent MAC-to-IP mappings is made using them.
Any device connected to the network can react to an ARP request, making it possible for an attacker to target computer A by responding to an ARP request with the IP address of their own device.
What are the consequences of a replay attack?
A replay attack is a type of cyber attack in which an attacker captures and then retransmits data packets in order to disrupt a legitimate communication. The consequences of a replay attack can be significant, depending on the nature of the attack and the systems that are targeted.
For example, if an attacker were to successfully launch a replay attack against a financial institution, they could potentially cause serious financial damage. In addition, replay attacks can also be used to gain access to sensitive information or systems, as well as to disrupt critical infrastructure.
As such, it is important for organizations to be aware of the risks posed by replay attacks and to put in place appropriate defences.
This includes ensuring that data packets are properly authenticated and encrypted, as well as implementing security measures such as intrusion detection and prevention systems.
How can you prevent replay attacks?
There are several things you can do to prevent replay attacks.
First, you can use a nonce, which is a number that is used only once. This ensures that each message has a unique value, making it more difficult for an attacker to replay a message.
Second, you can keep track of the messages that have been sent and received. This way, if a message is received more than once, you can detect it and take action accordingly.
Third, you can use encryption. This makes it more difficult for an attacker to eavesdrop on the communication and intercept messages. For this, we recommend VPN for its highly effective encryption methods.
Fourth, you can use digital signatures. This allows you to verify that a message has not been tampered with and that it comes from the expected sender.
Fifth, you can use time stamps. This puts a limit on how long a message can be replayed before it becomes invalid.
By using one or more of these methods, you can make it more difficult for an attacker to successfully launch a replay attack against your system.
Best Encrpytion VPN
HideIPVPN offers a VPN service with military-grade encryption, and high-speed servers with unlimited bandwidth.
Our service comes with shared IP addresses so that your activity can never be tied to one particular user, further protecting your privacy.
We also offer DNS leak protection, a Kill Switch, the latest VPN protocols, and a guaranteed no-log policy.
Best VPN Deal! Get HideIPVPN for $2.7/mo!
Every purchase you make comes with a 30-day money-back guarantee.
Conclusion
A replay attack is a type of network attack in which an attacker captures and then retransmits data in order to exploit a security flaw.
This can allow the attacker to gain access to sensitive information or perform other malicious actions. Replay attacks are notoriously difficult to defend against, but there are some measures that organizations can take to reduce their risk.



