What Is RSA Encryption? How Does It Work? [2022]
Last updated on July 8th, 2022 in VPN

Encryption is a technique used to protect data or communication from unauthorized access. RSA is one of the most popular and secure encryption algorithms available today. In this article, we’ll take a closer look at how RSA encryption works and why it’s such a powerful tool for keeping your information safe.
Table of contents
RSA encryption is a type of public-key cryptography that is used to encrypt data. It is one of the most popular algorithms used in this type of cryptography. RSA stands for Ron Rivest, Adi Shamir, and Len Adleman, who are the three people who developed the algorithm.
RSA works by using a public key and a private key. The public key can be known by anyone and is used to encrypt data. The private key is known only by the person who is receiving the data and is used to decrypt it.
When data is encrypted with the public key, it can only be decrypted with the private key. This makes RSA encryption very secure, as long as the private key is kept safe.
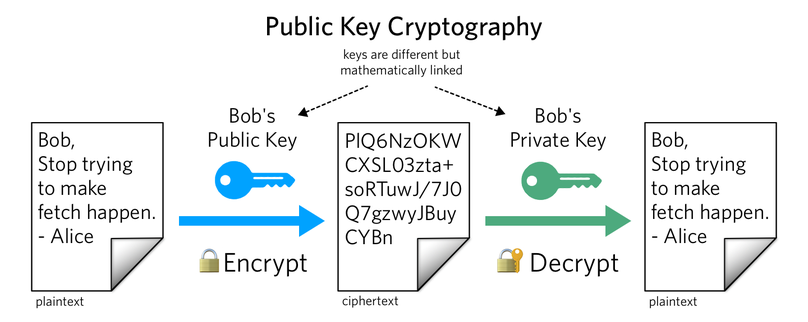
RSA encryption is a type of public-key cryptography, which is a method of communication that uses two keys to encrypt and decrypt data. One key is public, which means anyone can use it to encrypt data. The other key is private, which means only the recipient can use it to decrypt the data. RSA encryption is used in many different applications, such as email and file sharing.
The following is the RSA algorithm used to create public and private keys:
1. Pick two enormous prime numbers to stand in for the variables p and q.
2. To determine n, multiply the prime numbers. N will therefore be the modulus for encryption and decryption, with n = p x q.
3. Choose a number that is smaller than n to represent e. e and (p – 1) There is just one element that x (q – 1) share.
4. In order for e to be smaller than n, which e is a prime too, it must be bigger than 1.
5. As a result, the public key will be if n = p x q. (e, n). After then, this public key would be used to encrypt plain text communications.
6. Using the formula De mod (p – 1) x (q – 1) = 1 or De mod (n) = 1, where (d, n) is the private key, one can derive the private key.
In the majority of circumstances, you will be able to manage this algorithm by calling pre-written calculator functions through a development library. However, you might have to develop a function formula on your own to serve as your key calculator.
RSA encryption is used in a variety of situations, including securing communications, authenticating messages, and protecting data. It is also used in digital signatures and software validation. RSA encryption is a strong form of security that is used by businesses and individuals alike.
RSA encryption is frequently used in conjunction with other encryption protocols or for digital signatures that can verify a message’s integrity and validity. Because it uses more resources and is less effective than symmetric-key encryption, it is not typically used to encrypt complete communications or files.
A file is typically encrypted using a symmetric-key technique, followed by the RSA encryption of the symmetric key to improve efficiency. Only a party with access to the RSA private key will be able to decode the symmetric key using this method.
The original file cannot be decrypted unless the symmetric key is available. This approach can be used to safeguard files and messages without being time- or resource-intensive.
RSA encryption may be applied to a variety of technologies. OpenSSL, wolfCrypt, cryptlib, and a variety of other cryptographic libraries all support its implementation.
We owe a lot of our secure communications to RSA, one of the earliest widely adopted public-key encryption systems. It was the initial algorithm used in PGP encryption and was typically used in TLS. Numerous online browsers, email clients, VPNs, chat programs, and other communication tools still support RSA.
HideIPVPN offers a VPN service with military-grade encryption, and high-speed servers with unlimited bandwidth.
Our service comes with shared IP addresses so that your activity can never be tied to one particular user, further protecting your privacy.
We also offer DNS leak protection, a Kill Switch, the latest VPN protocols, and a guaranteed no-log policy.
Every purchase you make comes with a 30-day money-back guarantee.
RSA encryption is a type of public-key cryptography that is used to encrypt data and ensure its privacy. It is one of the most popular and widely used methods of encryption, and for good reason. RSA encryption has a number of advantages that make it an attractive choice for those looking to protect their data.
One of the biggest advantages of RSA encryption is that it is relatively simple to use. Unlike other types of encryption, which can be quite complex, RSA can be easily implemented by those with only basic knowledge of cryptography. This makes it an ideal choice for businesses and individuals who want to encrypt their data without having to invest a lot of time and resources into doing so.
Another advantage of RSA encryption is that it is very secure. Once data has been encrypted with RSA, it would take a very powerful computer many years to decrypt it. This makes RSA an ideal choice for businesses and individuals who need to protect their data from sophisticated hackers and other threats.
Finally, RSA encryption is also very flexible. It can be used to encrypt a wide range of data, including text, images, and even video. This makes it a good choice for those who need to encrypt sensitive information but don’t want to
RSA encryption is a powerful tool for securing information, but it also has its drawbacks. One of the biggest drawbacks is that it can be computationally intensive, which can make it impractical for some applications.
Additionally, RSA encryption is vulnerable to certain attacks, such as the man-in-the-middle attack, which can allow an attacker to intercept and alter communications.
 RSA is a public-key cryptography algorithm and is widely used in electronic commerce protocols. Its security is based on the difficulty of factoring large integers. However, RSA has been subject to a number of attacks and is not as secure as once thought.
RSA is a public-key cryptography algorithm and is widely used in electronic commerce protocols. Its security is based on the difficulty of factoring large integers. However, RSA has been subject to a number of attacks and is not as secure as once thought.
In 2012, a team of researchers from Stanford University and the University of California, Berkeley, showed that RSA keys generated by certain random number generators can be factored more easily than previously thought. This attack is known as the Dual EC DRBG attack.
In 2013, the NSA was revealed to have been using a number of techniques to weaken RSA encryption, including the use of backdoors and compromised random number generators.
These attacks have shown that RSA is not as secure as once thought. However, it is still widely used due to its relative ease of implementation and backwards compatibility with earlier versions of SSL/TLS.
Another asymmetric cryptosystem is the DSA (Digital Signature Algorithm). It was created in 1991 so that the federal government could utilize it as a more secure standard.
DSA’s use is not as widespread as RSA’s. Particularly for digital signatures, DSA is employed. In essence, the algorithm checks the message’s integrity and validity. As the fundamental components of a digital signature, DSA uses a combination of a private key and a hash.
The hash is only five to twenty symbols long, regardless of the file type or size. The message is authenticated using a hash. The hash will slightly shift to reflect changes if the communication is changed, interrupted, or falsified. This means that confirming the received hash is all that is required for verification.
To provide you with the answer to this one we have compiled a short list below:
1. RSA is a public-key encryption algorithm that is used in many different applications.
2. RSA is more secure than AES, but it is also slower and more resource-intensive.
3. RSA uses a different key for each message, so if one key is compromised, the others are still safe.
4. RSA keys can be generated offline, which makes them more secure than online key generators.
5. RSA keys can be used to encrypt and decrypt messages, as well as to sign and verify digital signatures.
When it comes to choosing an RSA encryption tool, there are a few things you need to take into account. Here are some tips to help you choose the right one for your needs:
– Make sure the tool offers strong encryption. The stronger the encryption, the more secure your data will be.
– Look for a tool that is easy to use. You don’t want to waste time trying to figure out how to use the tool.
– Choose a tool that is compatible with your operating system. This way, you won’t have any compatibility issues.
– Make sure the tool offers customer support in case you have any questions or problems.
RSA encryption is a Public-Key Cryptography algorithm that is used in many different applications today. It is an asymmetric key algorithm, which means it uses two different keys to encrypt and decrypt data. The RSA algorithm is very secure and has withstood the test of time, making it one of the most popular encryption algorithms in use today.