What is Crypto Malware? How to detect in 2024?
Last updated on July 20th, 2024 in General
 Cryptocurrency has been making headlines in recent years as a revolutionary way of conducting transactions online. However, with its growing popularity comes the rise of crypto malware. Crypto malware is a type of malicious software that targets cryptocurrency wallets and exchanges, stealing valuable digital assets from unsuspecting victims.
Cryptocurrency has been making headlines in recent years as a revolutionary way of conducting transactions online. However, with its growing popularity comes the rise of crypto malware. Crypto malware is a type of malicious software that targets cryptocurrency wallets and exchanges, stealing valuable digital assets from unsuspecting victims.
In this blog post, we will explore what crypto malware is, how it works. And, most importantly, how to detect and remove it from your system in 2024.
Read on to learn more about protecting yourself against this insidious threat!
Table of contents
Crypto malware, also known as cryptocurrency mining malware, is a type of malicious software that infects computers and uses their processing power to mine cryptocurrencies. This type of malware has become increasingly popular in recent years due to the rise in popularity and value of cryptocurrencies.
The way crypto malware works is by using the infected computer’s resources. The purpose is to solve complex mathematical problems that are required for validating transactions on the blockchain network. The more powerful the computer, the more valuable it is to hackers looking to profit from mining cryptocurrencies.
Unfortunately, crypto malware can be difficult to detect because it often runs silently in the background without any visible symptoms. One common sign of infection is a noticeable decrease in computer performance or an increase in CPU usage when running simple tasks.
To protect yourself against crypto malware, it’s important to keep your antivirus software up-to-date and avoid downloading suspicious files or clicking on unknown links. Additionally, installing ad-blockers and using VPN services can help prevent exposure to malicious websites that may contain crypto malware.
Understanding what crypto malware is and how it operates can help you take proactive measures towards protecting your devices from this growing threat.
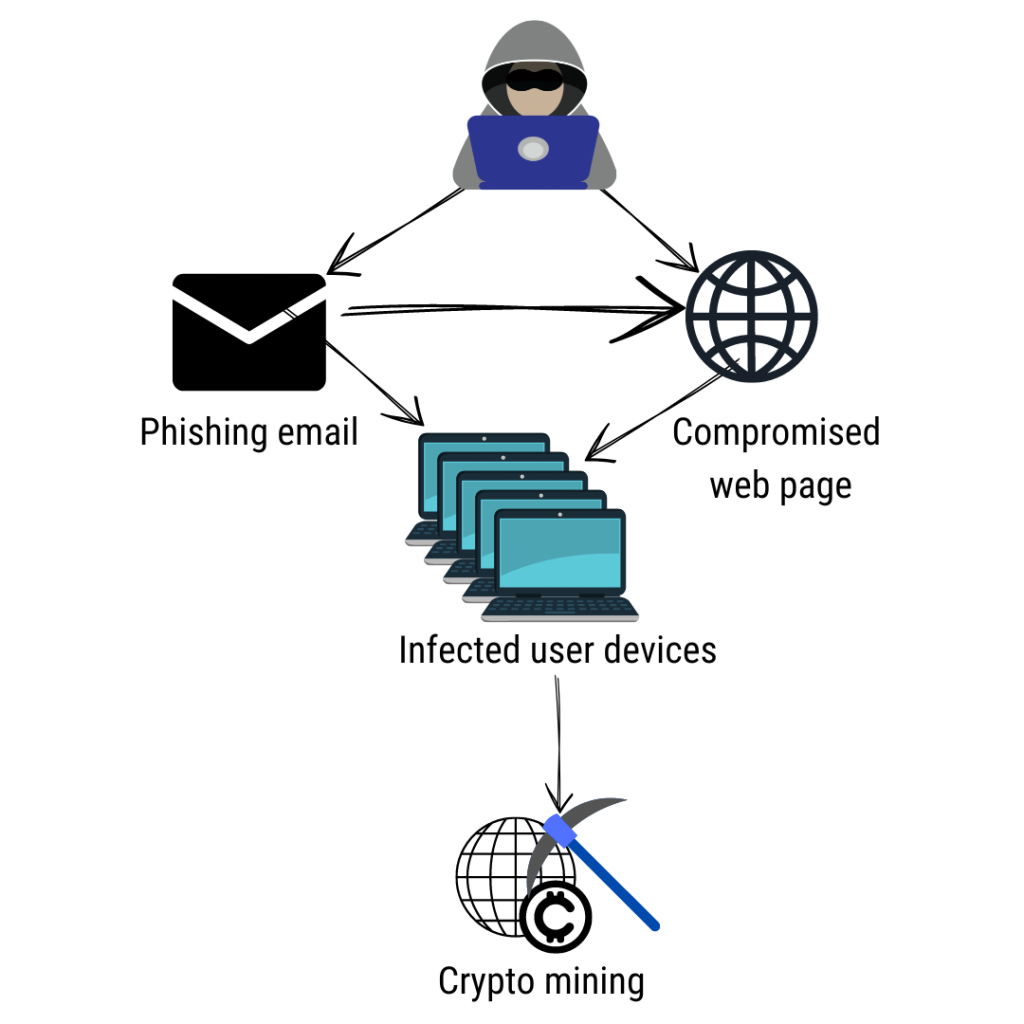 Crypto malware, also known as ransomware, is a type of malicious software that encrypts the victim’s files and demands payment in exchange for a decryption key. But how does this type of malware actually work?
Crypto malware, also known as ransomware, is a type of malicious software that encrypts the victim’s files and demands payment in exchange for a decryption key. But how does this type of malware actually work?
Crypto malware usually enters the system through phishing emails or infected downloads. Once it gains access to the system, it begins to infect all accessible files with encryption algorithms that are almost impossible to crack.
The next step involves displaying a pop-up message informing the user that their data has been encrypted and demanding payment for its release. The message may even include a countdown timer adding pressure on users to pay up quickly.
What makes crypto malware so dangerous is its ability to spread rapidly throughout networks and systems. This means that once one device is infected, other connected devices become vulnerable too.
In some cases, cybercriminals will attempt to extort large sums of money from companies by threatening not only to encrypt their data but also releasing sensitive information publicly if they refuse to pay.
Understanding how crypto malware works can help businesses take proactive measures against these attacks such as implementing strong cybersecurity protocols and employee training programs.
Crypto malware can infect your system in various ways, and detecting it can be challenging. However, there are some signs you can look out for to identify its presence on your computer.
One of the first things you should do is check for any unusual activity on your system. Crypto mining requires a lot of computing power, so if you notice that your computer has slowed down or is running hotter than usual, this could be an indicator of crypto malware.
Another sign to watch out for is unexpected pop-ups or ads appearing on your screen. These could be a result of malicious software attempting to mine cryptocurrency without your knowledge or consent.
You should also keep an eye on network traffic and monitor any suspicious connections from unknown IP addresses. This way, you can detect any unauthorized communication between your device and external sources.
Regularly scanning your system with anti-malware software can help identify and remove any potential threats before they cause significant damage.
By being proactive and vigilant in monitoring the activities on your computer, you increase the chances of catching crypto malware early before it causes serious harm.
 If you suspect that your system has been infected by crypto malware, it’s crucial to take immediate action to remove it. The longer the malware remains on your device, the more damage it can cause.
If you suspect that your system has been infected by crypto malware, it’s crucial to take immediate action to remove it. The longer the malware remains on your device, the more damage it can cause.
Firstly, disconnect from the internet and any other devices connected to your network. This will prevent the malware from spreading further and stealing additional information.
Next, run a full system scan using reputable anti-malware software. Make sure that your software is up-to-date with the latest virus definitions for optimal protection against new strains of crypto malware.
If the anti-malware detects any infections, follow its prompts to quarantine or delete them. Additionally, consider reinstalling any affected applications or restoring files from a backup made prior to infection.
To prevent future attacks, maintain good cybersecurity practices such as keeping all software up-to-date and avoiding suspicious downloads or attachments.
By taking swift action and implementing preventative measures, you can effectively remove crypto malware from your system and safeguard against future attacks.
One of the best ways to protect yourself against crypto malware is by using a VPN. A VPN, or Virtual Private Network, creates a secure and encrypted connection between your device and the internet. This means that all of your online activity is hidden from prying eyes.
When you use a VPN, all of your internet traffic is routed through an encrypted tunnel to a remote server. This makes it virtually impossible for cybercriminals to intercept and steal sensitive information like passwords, credit card numbers, or personal data.
Another advantage of using a VPN is that it can help you bypass geographic restrictions on websites and services. If you’re traveling abroad and want to access content that’s only available in your home country, for example, you can connect to a VPN server located there.
However, not all VPNs are created equal when it comes to protecting against crypto malware. It’s important to choose one with strong security features like encryption protocols such as OpenVPN or IKEv2/IPSec; kill switch feature which automatically disconnects the user if the internet drops; DNS leak protection; obfuscation technology which hides the fact that users are using a VPN connection.
By taking this simple step of using a reliable and trustworthy VPN service provider with robust security features in place, you can significantly reduce your risk of falling prey to crypto malware attacks while also enjoying enhanced privacy online.
HideIPVPN offers a VPN service with military-grade encryption, and high-speed servers with unlimited bandwidth.
Our service comes with shared IP addresses so that your activity can never be tied to one particular user, further protecting your privacy.
We also offer DNS leak protection, a Kill Switch, the latest VPN protocols, and a guaranteed no-log policy.
Every purchase you make comes with a 30-day money-back guarantee.
To sum it up, crypto malware is a growing threat that can cause significant damage to individuals and organizations alike. It’s important to stay vigilant and take necessary precautions to protect your system from such attacks.
By implementing security measures like using VPNs, updating software regularly, and being cautious of suspicious emails or websites, you can significantly reduce the risk of falling victim to crypto malware.
If you suspect your system has been infected with crypto malware, act quickly by running a virus scan and seeking professional help if needed. Remember that prevention is always better than cure when it comes to cyber threats like these.
Stay informed about the latest developments in this field and adopt best practices for keeping your sensitive data safe. By staying ahead of the curve, you can safeguard yourself against potential threats while enjoying all the benefits that modern technology has to offer.