What is AES encryption? [2022]
Last updated on July 5th, 2022 in VPN

AES encryption is a type of data encryption that is used to protect information. It is a symmetric-key algorithm, which means that the same key is used to encrypt and decrypt the data. AES was developed by two Belgian cryptographers, Joan Daemen and Vincent Rijmen. AES was adopted as an industry-standard in 2002 by the U.S. National Institute of Standards and Technology (NIST).
AES encryption is considered to be very secure. The key length can be 128, 192, or 256 bits long. The longer the key, the more difficult it is to break the encryption. AES encryption is used in many different applications, including VPNs, disk encryption, file encryption, and more.
Table of contents
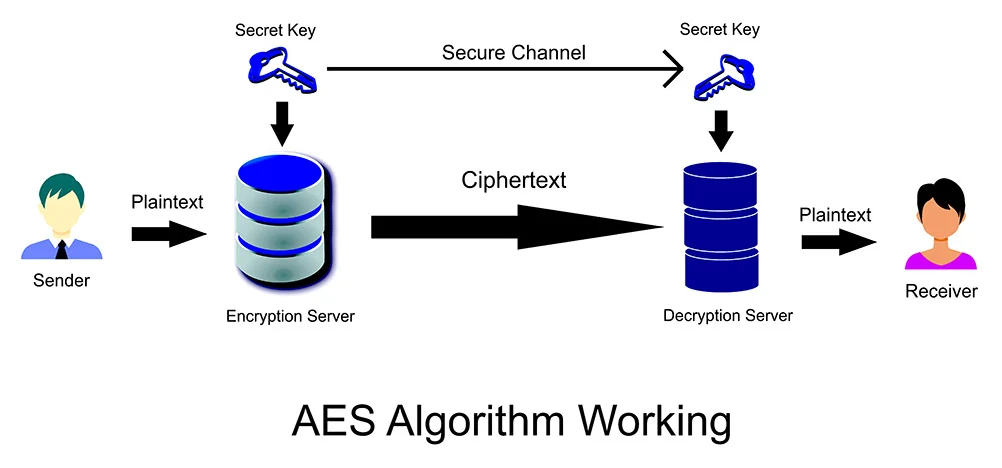
via Trentonsystems
AES encryption is a type of symmetric-key encryption that uses a key of 16 bytes. It is a relatively new technique, but has already been adopted by the U.S. government and is now used by many organizations and individuals to protect their data.
AES encryption is very secure and is not vulnerable to the same kinds of attacks that can break other types of encryption. The key is also very difficult to crack, even with powerful computers.
AES is a block cipher that uses 128-bit, 192-bit, or 256-bit keys to encrypt and decode data in blocks of 128 bits. The same key is utilized for both data encryption and decryption, as was already mentioned. Many times, AES is referred to as AES-128, etc., when it uses a 128-bit key.
An explanation of how AES operates:
Multiple rounds of encryption are used to protect data, and each round entails a number of mathematical operations.
Starting with the initial secret key, a succession of fresh round keys is generated using Rijndael’s key scheduling method. Key expansion is what we call this.
All the actions required to encrypt data are simply carried out backward to decode it. To reverse the procedure using each inverted round key, you need the original secret key.
AES encryption is very secure. It has been tested by many organizations and has been found to be very effective at keeping data safe.
Given existing and expected technology, brute-forcing AES-128 would take longer than the lifespan of the universe, as we have already discussed.
Bruce Schneier, a renowned cryptographer, has even asserted that AES-128 may be stronger than AES-256 due to its stronger key scheduling (the algorithm that calculates all the round keys from the original secret key).
The “gold standard” for symmetric-key encryption, however, is AES-256. Why? Optics does come into play to some extent. Simply put, AES-256 sounds more impressive than AES-128 and “common sense” tells us it must be more robust.
AES encryption is a powerful tool that can help keep your data safe. Here are some of the benefits of using AES encryption:
1. AES encryption is incredibly strong. It is virtually impossible to break AES encryption, making it ideal for protecting sensitive data.
2. AES encryption is fast and efficient. It can be used to encrypt large amounts of data quickly and easily.
3. AES encryption is compatible with a wide range of devices and software. This means that you can use AES encryption to protect your data no matter what type of device or software you are using.
4. AES encryption is easy to use. There are a number of different ways to encrypt data using AES, so you can choose the method that best suits your needs.
As one of the most popular forms of encryption, AES encryption is used by both businesses and individuals to protect data. However, AES encryption is not without its challenges. One of the key challenges is keeping data secure while it is in transit. This is because data is vulnerable to interception while it is being sent from one location to another. To combat this, businesses and individuals often use VPNs or other secure network protocols to protect data in transit.
Another challenge of AES encryption is protecting data at rest. This means ensuring that data is secure when it is stored on devices such as computers, servers, and portable storage devices. To do this, businesses and individuals can encrypt their data using software that utilizes AES encryption. Additionally, they can also physically secure their devices by keeping them in a safe location or using security features such as password protection and biometric authentication.
Despite the challenges, AES encryption remains a popular choice for businesses and individuals who need to protect their data. By understanding the challenges and taking steps to mitigate them, businesses and individuals can ensure that their data is protected from theft or unauthorized access.
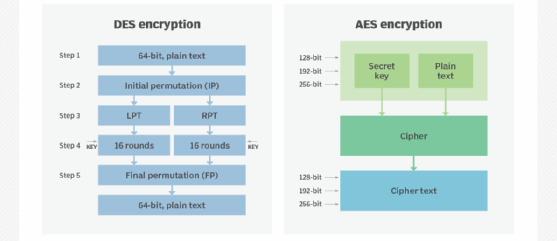
AES is a fairly safe encryption scheme, however, it does have certain theoretical flaws (it would take billions of years even for organizations with tons of computing power, such as the National Security Agency).
AES encryption has never been broken by basic brute-force attacks, but if it is implemented incorrectly, it may be the subject of other, more sophisticated sorts of attacks.
By employing sheer force, it is practically impossible to crack AES 256. AES would take billions of years to break using current computing capability, in contrast to a 56-bit DES key, which can be cracked in less than a day. It would be ridiculous for hackers to even consider such an attack.
However, no encryption method is 100 percent secure. Those who have probed AES have discovered a few potential entry points. They identified a potential related-key attack in 2009. This kind of cryptanalysis looks at how a cipher functions with various keys in an effort to break it. Fortunately, only improperly set up AES systems are at risk from the related-key attack.
AES 128 was the target of a known-key distinguishing attack that same year. The attack made use of a known key to figure out how the encryption was put together. The regular 10-round version of AES 128 was not the objective of the hack, therefore it would not pose a serious threat.
Many theoretical attacks on AES keys have been reported over the years, but all of them are either impractical in real-world settings or only successful with AES implementations that use less rounds.
The most effective effort was a biclique attack that was disclosed in 2011 and can cut the time required to brute force AES by a factor of four. However, brute-forcing AES on any presently known or future computer technology would still take billions of years.
AES-128 or higher can withstand no practical key attack when correctly implemented.
The primary risk comes from side-channel assaults because the AES cipher is so secure on its own. These aim to gather information the system is leaking rather than making a brute-force attack.
To try to figure out how the security algorithms function, hackers can listen in on sounds, electromagnetic signals, time data, or power use.
By eradicating information leakage or concealing the leaked data (by producing additional electromagnetic signals or sounds), side-channel attacks can be avoided. These side-channel dangers can be avoided by carefully implementing AES.
AES-256 and XChaCha20 encryption vary primarily in that AES-256 is a block cipher and XChaCha20 is a stream cipher. AES encryption has a solid reputation (thus the term “advanced encryption standard”), but XChaCha20 is still a relatively new technology.
AES-256 encryption, however, is a little more difficult than XChaCha20, which has a number of drawbacks:
The probability that someone may screw up the algorithm and compromise data increases with algorithm complexity.
In contrast to XChaCha20, AES-256 requires specialized hardware acceleration to function properly. For instance, the latest ARM CPU versions, AMD, and Intel enable AES.
AES encryption is not supported by previous generation CPUs, which are typically found on entry-level Android devices like Android Go phones, smart TVs, and wearables. AES-256 may be many times slower than XChaCha20 without specialized gear.
It’s a good thing that Wireguard now uses ChaCha20 algo and HideIPVPN supports Wireguard as well, so you’re all covered if you want to use a VPN with top-of-the-line encryption.
HideIPVPN offers a VPN service with military-grade encryption, and high-speed servers with unlimited bandwidth.
Our service comes with shared IP addresses so that your activity can never be tied to one particular user, further protecting your privacy.
We also offer DNS leak protection, a Kill Switch, the latest VPN protocols, and a guaranteed no-log policy.
Every purchase you make comes with a 30-day money-back guarantee.
AES encryption can be used by developers in the following situations:
AES encryption is a type of Symmetric-key cryptography, which means it uses the same key to encrypt and decrypt data. It is a popular choice for data encryption because it is incredibly secure, and even the US government relies on it to protect classified information. If you are looking for a reliable way to encrypt your data, AES is definitely worth considering.